 After 10 years of continued expansion in the security awareness space and providing our platform to tens of thousands of customers, we have observed a certain progress of organizational security awareness over time.
After 10 years of continued expansion in the security awareness space and providing our platform to tens of thousands of customers, we have observed a certain progress of organizational security awareness over time.
The speed of this progress is different by org size, geolocation, and industry, but we see this same pattern return over and over. In certain cases some steps are omitted. In other cases a few steps are taken at the same time. Ultimately however, most orgs see the same ultimate ideal scenario. Let's step through these 10 phases and you can determine where you are in your own organization in this process:
- Increased Technical Awareness for Infosec and IT Pros
Infosec and IT Pros feel the pain first. Infected workstations and ransomware attacks keep them on the defense and backlogged. Many of these professionals see the need for security awareness, but sometimes have been discouraged by the unworkable old-school practice of stepping users through 15 minutes of compliance-driven training. Quite a few of these pros understand the risks of relying on software-driven controls only. - Awareness Content Delivery for end-users
Here is where first-generation training videos replace the break-room death-by-PowerPoint presentations, usually not very well trackable but it's a start. - Platform Automation Enables Compliance Requirements
Automating the process of training delivery through a (in- or external) Learning Management System (LMS) so that compliance requirements are easier to fulfill. This is very dependent on the size of the org; larger ones have an on-prem or cloud-based LMS used for general training purposes. - Continuous Testing
This phase demonstrates a significant shift toward the 'Zero Trust' model where the employee after training gets tested frequently to make sure that the acquired knowledge has actually become a skill that is applied in practice and does not disappear over time (use it or lose it). - Security Stack Integrations
At this stage, "phish alert buttons" are deployed to the end-users' email client so that they can report any phishy emails to the Incident Response team or SOC who can then take action. - Security Orchestration
The next phase is that these reported emails are integrated into a security workstream which quickly evaluates the risk level and in case an active attack is in progress, can automatically reach into the inbox of all users and rip out malicious messages before further damage is done. - Advanced User Behavior Management
Having in-depth risk metrics about both individual and groups of users, orgs can now create tailored campaigns based on observed risky behavior. An example is scanning the dark web for breached org credentials, bad password usage and send individual training modules to those high-risk users. - Adaptive Learner Experience
The next phase is the end-user having a localized UI where they go and can see their individual risk score, get badges, and start to participate in the learning experience. Also, this phase is when advanced metrics allow AI-driven campaigns where each user gets highly individualized security awareness training. - Active User Participation In Security Posture
Here is where the user becomes aware of their role in your orgs' defense and actively chooses additional training to reduce their risk score. They participate in awareness campaigns, become a local awareness champion, and understand they themselves have become the endpoint. - Human Endpoint As Strong Last Line Of Defense
The ultimate state where each employee is sufficiently aware of the risks related to cyber security, and makes smart security decisions every day, based on a clear understanding of those risks. The current WFH environment has accelerated the need for this significantly.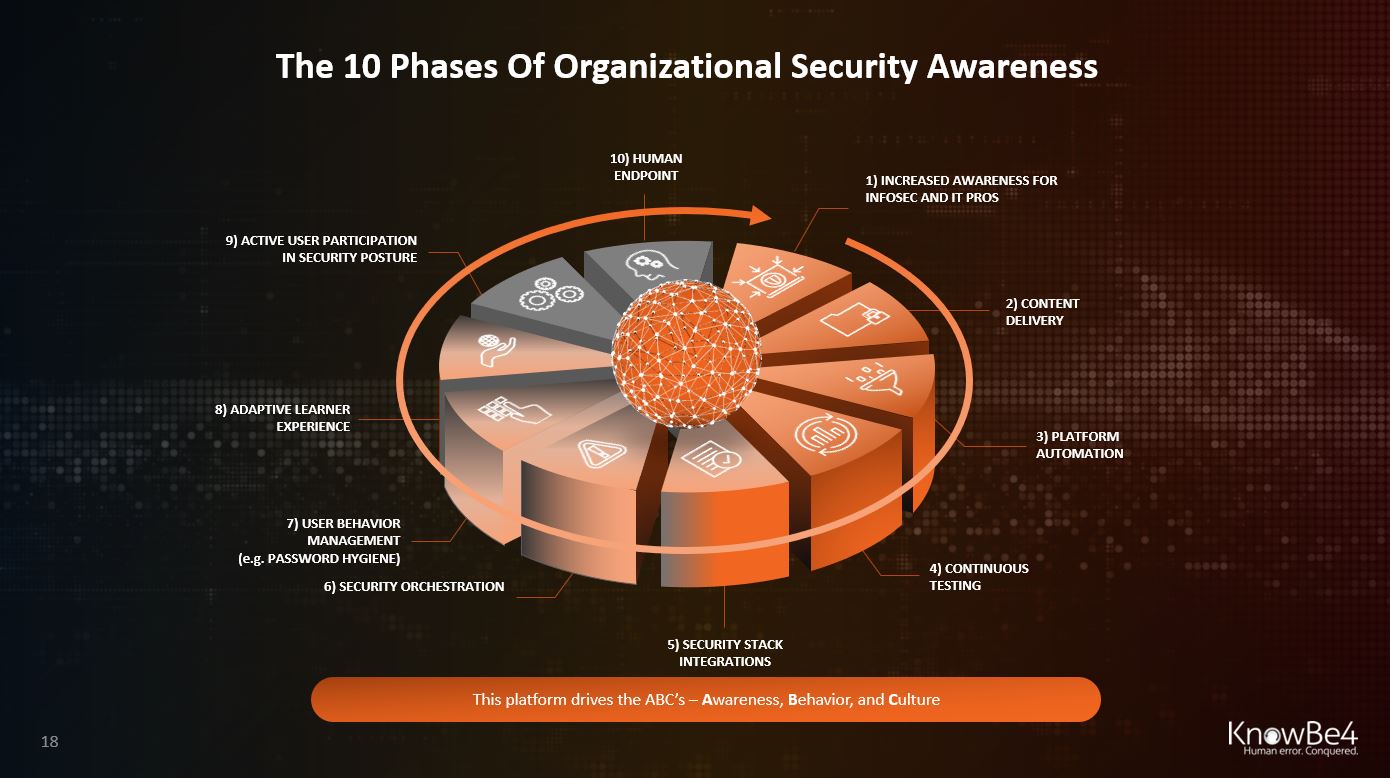
 Here's how it works:
Here's how it works:




