TeslaCrypt is a relatively new ransomware variant which has made it in the Top 5, and has rapidly innovated in its efforts to evade detection. The latest version which is one of the most sophisticated ransomware strains out there, lets criminals use unique file encryption keys for each infected victim, eliminating the possibility that one single key could be used to unlock different victims.
The folks at the Cisco Talos blog have reversed engineered this latest version and if you are into crypto they have a tough cryptographic journey waiting for you here. Fasten your seatbelts. They start out by explaining in a simplified way how the real encryption algorithm of TeslaCrypt 3 works. Here is a picture:
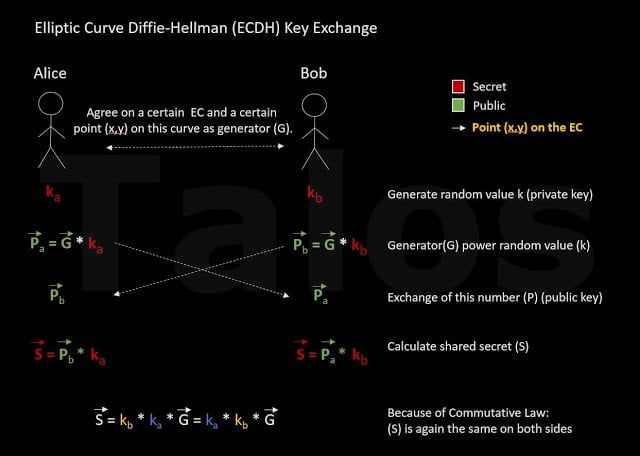
- First the adversaries generate the public key (Pb) and include it in the ransomware binary file which later on infects the PC (Alice).
- The ransomware on the infected PC (we call it Alice from now on) can now calculate a random value (ka).
- This means Alice has everything to calculate the shared secret
(S = Pb * ka). - Alice now encrypts all files with a temporarily generated AES key.
- Alice then encrypts this temporary AES key with the (x-coordinate of the) shared secret (S) from step 3. We will call this encrypted AES key the 'recovery key'.
- Now the trick: after the encryption is done, Alice's private key (ka) and the shared secret (S) is deleted. This means that Alice can no longer calculate the shared secret(S) using the equation S = Pb * ka to decrypt the recovery key.
- BUT, the shared secret can still be restored by using the equation from Bob's side: S = Pa * kb. Unfortunately, Alice does not have Bob’s (the C&C server) private key (kb). Only the C&C server has it. This means only the C&C server can perform the calculation. Alice (the victim) pays the ransom and sends her public key (Pa) to the C&C server. Now it can send the calculated shared secret back to Alice to decrypt the recovery key.
In practice TeslaCrypt 3 is using a more complex implementation. Read the article at Talos!
Concerned about ransomware infections caused by end-users? Get the most informative and complete ransomware hostage rescue manual. This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware.





