We are seeing a big phishing wave with a social engineering attack that threatens with a personalized lawsuit using the domain name of the targeted victim. This is an interesting payload -- very sophisticated. You can wait a week or two and you will find ransomware added to this noxious package.
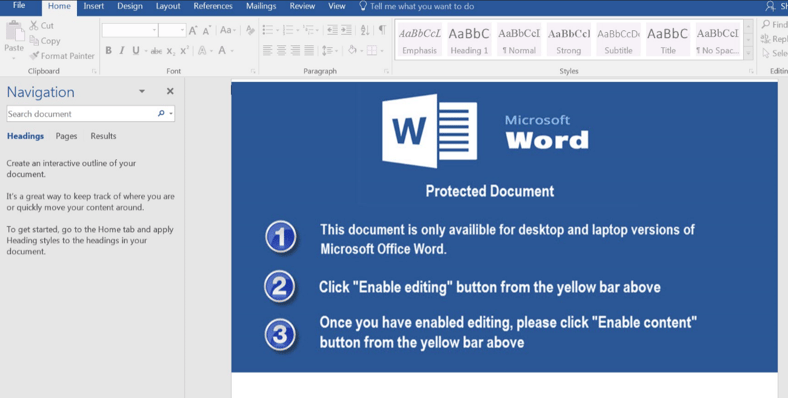
As usual, the Word doc does contain an embdedded macro, which the user is prompted to "Enable."
But instead of reaching out to an external server and pulling down a malicious .EXE to run (what most malicious macros do), this macro unpacks and decrypts an .EXE that's cleverly embedded in the .DOC itself. It then drops a file named WinHost32.exe in the \System32 folder and executes it.
That malicious .EXE is Hancitor, a Trojan downloader currently being used to distribute the Pony infostealer Trojan as well as the Vawtrak banking Trojan.
This unusual scheme for using a Word macro to deliver an embedded .EXE has been covered in several (somewhat technical) blog posts incliding Palo Alto Network's research center and Barkly. Barkly is anticipating that the malware gang behind Hancitor will begin using it to distribute Locky/Zepto ransomware in the near future.
News articles (less technical) from Threatpost and Helpnet Security discuss how this new approach of embedding the malicious code encryption into Visual Basic allows the malware to stay undetected for a longer period of time against most antivirus products.
Note that just yesterday we blogged about a version of RAA ransomware being delivered through a monster .JS file that contained within itself embedded ransomware code as well a copy of the Pony infostealer trojan. Combine that with the new version of Locky that uses an embedded RSA key... and we can see the dim outlines of what appears to be a trend: an effort by the bad guys to reduce the amount of network traffic required to successfully mount a malware-based attack on target PCs. Doing so leverages the value of 0 day malcode by decreasing the attack surface available to anti-malware solutions.
This is how the Word Doc looks:
Are you aware that many of the email addresses of your organization are exposed on the Internet and easy to find for cybercriminals? With these addresses they can launch social engineering, spear-phishing and ransomware attacks on your organization. The Email Exposure Check (EEC) is a one-time free service. Sign up for your free EEC and find out now which of your email addresses are exposed.
Don't like to click on redirected buttons? Cut & Paste this in your browser:





