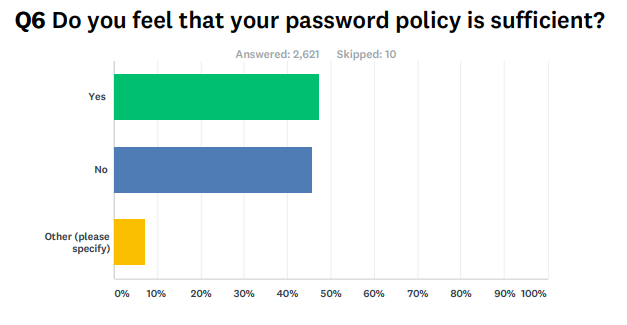
After the NIST passwords bombshell, we surveyed 2,600 IT professionals to find out how they were managing passwords. The answers show that IT Pros are generally receptive to the proposed pass phrase concept suggested by NIST.
NIST Special Publication 800-63B, “Digital Identity Guidelines,” states: “Many attacks associated with the use of passwords are not affected by password complexity and length. Keystroke logging, phishing, and social engineering attacks are equally effective on lengthy, complex passwords as simple ones. This means that password complexity has failed in practice." Verizon's latest Data Breach Report showed that 81% of hacking-related breaches used either stolen and/or weak passwords, supporting the NIST conclusion.
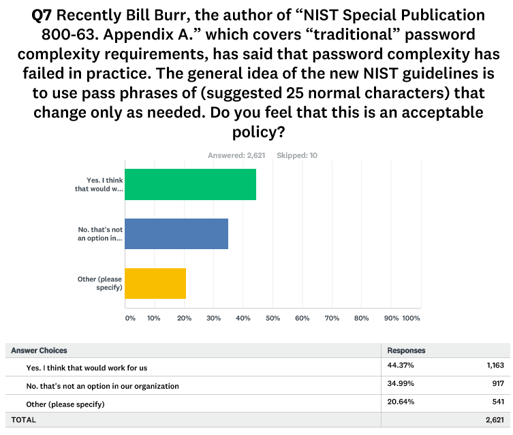
KnowBe4’s survey showed that 44% of respondents overall, (large organizations with 1,000+ employees and small to mid-size businesses), think a roughly 25-character pass phrase could work versus 35% who don’t believe it to be a viable option for their organization. Here are the survey results (PDF) The highlights from the survey are:
- Nearly 97% of large organizations have an enforced password policy compared to almost 88% in small to mid-size organizations.
- A majority (63%) of organizations do not allow password re-use, however this does not prevent employees from using the same password on multiple sites.
- Almost half (49%) of large organizations believe their current password policy is insufficient, while 48% of small to mid-size organizations believe their password policy is good enough.
- Enterprise-size organizations (1,000+ users) prefer multi-factor authentication (MFA) with only 38 % stating they do not use it, compared with 62 percent in Small and Medium organizations not using MFA.
Bill Burr, former NIST (National Institute of Standards and Technology (NIST) engineer who wrote the password complexity requirement said the 2003 standards had failed in practice. With multiple devices, accounts and websites, the average user has somewhere around 27discrete passwords to remember.
“Passwords are a known weakness in corporate security and have come under more intense scrutiny recently. Most organizations have password enforcement in place, but most aren’t taking it seriously enough by not enforcing policies beyond the normal number and letter character minimum and not requiring multi-factor authentication,” said Stu Sjouwerman, CEO of KnowBe4. “It is well-known that employees are the weakest link in security and that includes password usage. IT can’t expect employees to put password policies in place on their own. It’s an effort that IT must lead.”
KnowBe4 encourages companies to test their password enforcement with a free tool to find out how exposed their users are with its Weak Password Test.
 How weak are your user’s passwords? Are they... P@ssw0rd?
How weak are your user’s passwords? Are they... P@ssw0rd?
Verizon's recent Data Breach Report showed that 81% of hacking-related breaches used either stolen and/or weak passwords. Employees are the weakest link in your network security, using weak passwords and falling for phishing and social engineering attacks.
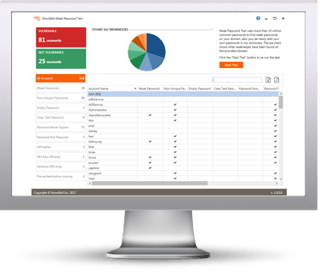
KnowBe4’s complimentary Weak Password Test (WPT) checks your Active Directory for several different types of weak password related threats.
WPT gives you a quick look at the effectiveness of your password policies and any fails so that you can take action. WPT tests against 10 types of weak password related threats for example; Weak, Duplicate, Empty, Never Expires, plus 6 more.
Here's how Weak Password Test works:
- Reports on the accounts that are affected
- Tests against 10 types of weak password related threats
- Does not show/report on the actual passwords of accounts
- Just download the install and run it
- Results in a few minutes!
This will take you 5 minutes and may give you some insights you never expected!
Download Here:
or cut & paste this link in your browser: https://info.knowbe4.com/weak-password-test
Thanks very much in advance !
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc.






