 With threat actors honing their trickery skills to craft the perfect email used to fool a would-be victim recipient, new data shows cybercriminals are stepping up their game on a number of fronts.
With threat actors honing their trickery skills to craft the perfect email used to fool a would-be victim recipient, new data shows cybercriminals are stepping up their game on a number of fronts.
Spear phishing only works when the misleading email content is relevant to the recipient. It’s one of the reasons social engineering plays such a critical role in today’s email-based attacks. According to security vendor Barracuda’s latest report, Spear Phishing: Top Threats and Trends, organizations are experiencing far more convincing and impactful campaigns that are focused on a wider range of roles in the organization than ever before:
- 1 in 10 attacks are Business Email Compromise (BEC) attacks
- 77% of BEC attacks target employees outside of finance and executive roles
- Even so, the average CEO receives 57 targeted phishing attacks each year
- IT staff still receive an average of 40 per year
- Microsoft remains the top impersonated brand with WeTransfer in at number two
According to Barracuda, the roles targeted within an organization extend well-beyond that of the CEO or IT, making every employee a potential target:
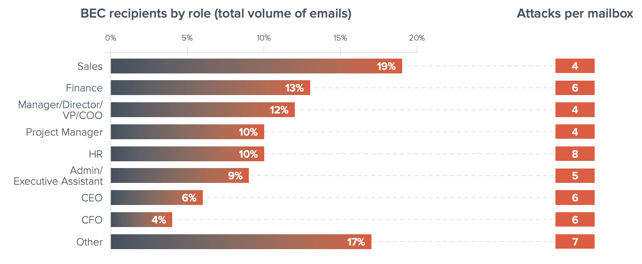
Source: Barracuda
This is the very reason why it’s so important to ensure that every user – regardless of role – continually takes part in your Security Awareness Training program. By doing so, they will remain updated on the latest scams, campaigns, social engineering tactics, etc. and be able to quickly identify malicious email content and avoid being the person responsible for a successful cyberattack.
 Here's how it works:
Here's how it works:




