 As most readers are undoubtedly aware, President Donald Trump has been de-platformed by major social media companies, including Twitter and Facebook, following events at the U.S. Capitol in Washington D.C. on Wednesday, January 6.
As most readers are undoubtedly aware, President Donald Trump has been de-platformed by major social media companies, including Twitter and Facebook, following events at the U.S. Capitol in Washington D.C. on Wednesday, January 6.
There is one social media platform that remains open to Trump, though: Parler, which bills itself as a "free speech" alternative to the large social media companies that have dominated the online landscape.
Parler is facing challenges of its own, however. Both Apple and Google have now removed the social media app -- popular with Trump supporters and other political conservatives -- from their respective app stores. Amazon has followed with an announcement that it is booting Parler from its web hosting services.
An Opportunity for Bad Actors
These actions come at a perilous time in the United States. Emotions in this country are at a boiling point following the events in D.C. With the near simultaneous suspension of Trump from Twitter and other social media platforms and the removal of Parler from app stores, many users will be highly motivated to find alternative sources to download and access Parler. And that represents a golden opportunity for malicious actors to exploit.
We anticipate that bad actors will fill the gap by launching phishing campaigns that offer users bogus web sites with fake, malicious Parler downloads or even malware-infected versions of Parler. They may also set up fake web sites and push malicious online advertising to do the same.
Parler-themed phishing emails could take at least two forms:
- spoofed Parler emails offering alternative download/install links;
- fake right wing/conservative emails denouncing the actions of Google and Apple and offering alternative download/install links.
It's worth noting that there are now news reports that Parler was hit by a massive data scrape before it went dark Monday morning. As a result, 70 TB of Parler data has been leaked online. That data dump reportedly includes user profile data, user information, admin rights data, videos, and posts (including deleted posts).
This massive haul of leaked data could allow malicious actors to individually target Parler users in spear phishing campaigns as well as all manner of online scams.
Our Response
In response, KnowBe4 has developed a handful of simulated phishing emails that customers of our KMSAT security awareness training platform can use to "inoculate" their employees.
The first spoofs Parler itself:
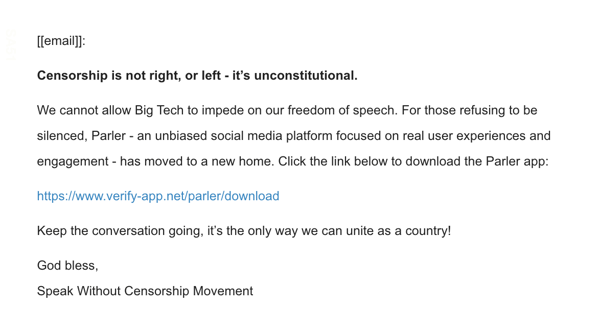
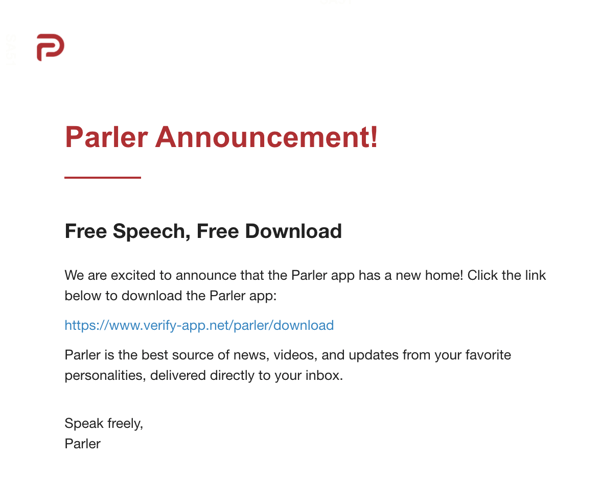 The second denounces the removal of Parler from app stores and Amazon's web hosting services:
The second denounces the removal of Parler from app stores and Amazon's web hosting services:
 These new templates are now available to customers in the "Controversial/NSFW" category of KnowBe4's template collection. We may develop additional templates to reflect other social engineering schemes that could be used to target Parler users.
These new templates are now available to customers in the "Controversial/NSFW" category of KnowBe4's template collection. We may develop additional templates to reflect other social engineering schemes that could be used to target Parler users.
What You Can Do Now
In addition to using these new templates to phish your users, it would also be a good idea to alert your employees and users to the danger that they could be encountering phishing emails as well as fake web sites and deceptive online advertising offering them alternative download sources for Parler that, in reality, will be pushing malware instead.
You are welcome to quote and re-purpose the text in this blog post to warn your users and advise them to click the Phish Alert Button (PAB) to alert admins should they encounter any email they suspect to be malicious.
 Here's how it works:
Here's how it works:
