 A phishing campaign is targeting African banks with a technique called “HTML smuggling” to bypass security filters, according to threat researchers at HP.
A phishing campaign is targeting African banks with a technique called “HTML smuggling” to bypass security filters, according to threat researchers at HP.
“In early 2022, an employee of a West African bank received an email purporting to be from a recruiter from another African bank with information about job opportunities there,” the researchers write. “The domain used to send the email was typosquatted and does not belong to the legitimate mimicked organization. A WHOIS request reveals the domain was registered in December 2021 and visiting the website returned an HTTP 404 “Not found” response. To make the lure more credible, the threat actor also included a reply-to address of another supposed employee of the recruiting bank.”
The attackers use HTML smuggling to evade security technologies and deliver their phishing emails to employees’ inboxes.
“HTML smuggling is a technique that enables attackers to sneak file formats that would otherwise be blocked past email gateways by encoding them in an HTML file,” the researchers write. “JavaScript blobs or HTML5 download attributes can be used to decode and reconstruct the file. When the user opens the HTML attachment using a web browser, they are prompted to download the file, which is already stored on the local system. This way HTML smuggling bypasses security controls that block malicious website traffic, such as web proxies. The technique is dangerous because HTML email attachments are not typically blocked at gateways and detecting the encoded malware can be challenging. Using this technique, dangerous file types can be smuggled into an organization and lead to malware infection.”
The goal of this phishing campaign is to deliver the Remcos RAT, which will give the attackers a foothold within the organization’s network from which they can deploy ransomware or launch additional social engineering attacks.
“Remcos is a commercial Windows remote access tool (RAT) that gives the operator significant control over the infected system,” the researchers write. “Its capabilities include running remote commands, downloading and uploading files, taking screenshots, recording keystrokes and recording the user’s webcam and microphone.”
New-school security awareness training can enable your employees to thwart social engineering attacks.
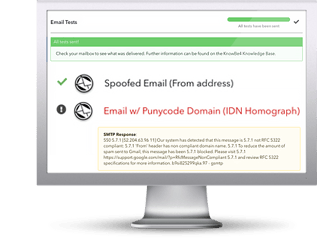 Here's how MSA works:
Here's how MSA works:




