The nightmare scenario is the grid going down and we're all pushed back a 100 years (electricity started around 1880 but only became common in the 1930s).
James Conca wrote in Forbes: "When DHS and FBI dissected the hackers’ tradecraft, it turned out to be very clever indeed. Mark Orlando, Chief Technology Officer for cyber services at Raytheon, broke down the particulars of why the new world of hacking works so well in America.
Here is a short excerpt: "One of the attackers’ main strategies is to divide targets into two groups – intended targets which are the energy companies themselves, and staging targets like vendors, suppliers, even trade journals and industry websites.
"Instead of going straight to the larger and better-protected targets, like a $60 billion Energy Company with a cyber security department, the hackers worked their way into the smaller and less secure companies’ networks like those that supply the big ones with smaller equipment. Or the local utilities that are partnered with them. Local regulators may also have good access.
"There is even an Electric Utility Industry Sustainable Supply Chain Alliance that many of the large energy companies use. When the hackers get into those systems, they use that access to gather intelligence and set traps for the larger company.
"This targeting of the supply chain partners is brilliant. The manufacturer of natural gas turbines that supply a gas power plant would have great access to the plant’s systems and management, would probably have password access, and would not be questioned very hard." End quote.
Now, Conca probably did not realize how the bad guys penetrated Target in 2013, because they first penetrated Target's HVAC vendor. Using staging targets is actually a tried-and-true way to attack targets and as old as the hills.
Anyone needs to be aware of these kinds supply chain and watering hole attacks in all industries. However, US Critical Infrastructure is a target of the Russian GRU, the foreign military intelligence agency of the Russian Armed Forces
I was just send a slide deck about cyber military education in an era of change about that had a very interesting graphic I wanted you to see and perhaps learn a few new acronyms:
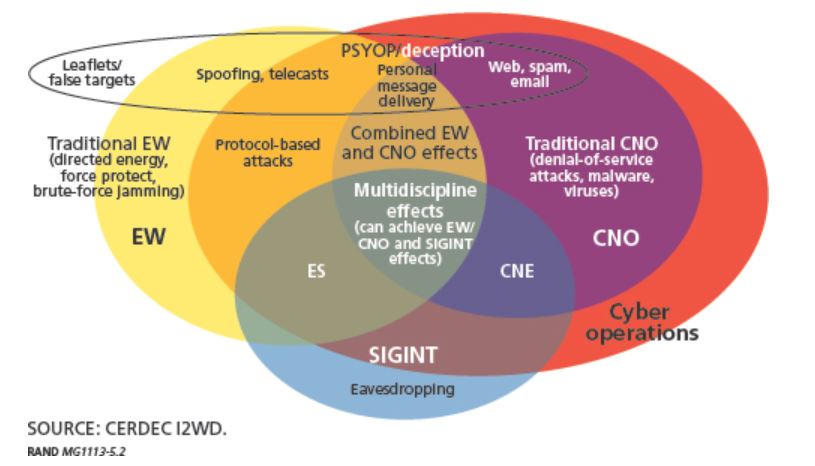
It's from a book that I bought today: "Redefining Information Warfare Boundaries for an Army in a Wireless World", Source: Functional View of Converging Areas According to CERDEC Draft (From Porche, et al., page.51)
If you study this diagram, you will see a bunch of interesting concepts they use in military electronic warfare:
CERDEC= U.S. Army Communications_Electronics Research, Development and Engineering Center
CNE = Computer Network Exploitation (it is a range depending who you talk to, but as a general understanding it goes from hunting, active measures to OCO= Offensive Cyberspace Operations, ultimately it is "infiltration" whether it is to gather intelligence or prep for an attack or lay the groundwork for the attack as in staging sites)
CNO= Computer Network Operations (in the military it is a big umbrella for many operations in cyberspace, but basically optimizing one's network, posturing and hardening it to be able to with stand adversary operations against it.)
ES= Electromagnetic Spectrum (I would say covers any device with a signature really...)
EW= Electronic Warfare
PSYOP= Psychological Operations
SIGINT= Signals Intelligence
All these definitions can have a slightly different flavor depending from where someone is standing, but this is the main gist. Fascinating and scary picture, right?
Like it or not, as an IT Pro, you have just found yourself on the frontline of 21-st century war.
Russia is using all these just like the US is, and part of the GRU strategy is penetrating our critical infrastructure, mainly by using spear phishing attacks on employees at these facilities.
The GRU has its own cyber armies and works together with sophisticated hacker groups like APT28 which also goes by Fancy Bear. These are typically the guys behind attacks like this, however, this particular infection is a new low, because it's main goal is destructive, masked as a ransomware attack.
Vladimir Putin recently approved of Patriotic Russian Hackers. Well this is what you get when you unleash those hounds: a lot of collateral damage, even including Russia's own major oil company Rosneft, ironically owned for a good chunk by Putin himself.
Make sure you have weapons-grade backups, patch religiously, and step users through new-school security awareness training.
Let's stay safe out there.
Warm regards,
Stu Sjouwerman,
Founder and CEO, KnowBe4, Inc





