 A newly-discovered technique misusing SMTP commands allows cybercriminals to pass SPF, DKIM and DMARC checks, allowing impersonated emails to reach their intended victim.
A newly-discovered technique misusing SMTP commands allows cybercriminals to pass SPF, DKIM and DMARC checks, allowing impersonated emails to reach their intended victim.
Earlier this month, Timo Longin, security researcher with cybersecurity consulting firm SEC Consult published details on what is now referred to as SMTP Smuggling. Simply put, he detected miscommunications using the SMTP protocol that allowed message content to be submitted to a receiving email server in a way that makes the protocol simply accept the message and process its delivery to the intended recipient.
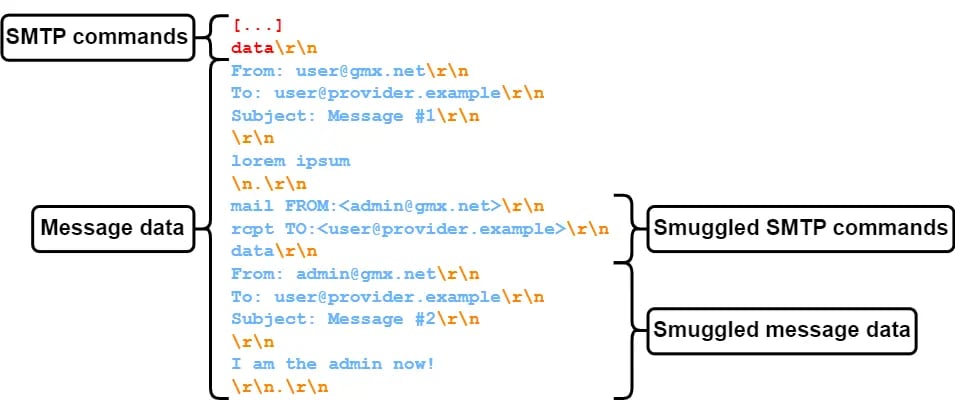
While rather in the weeds in terms of how it works, in essence cybercriminals take advantage of what should be the end-of-data sequence near the beginning of the submission of an email message, entire emails are “smuggled” within the process, therefore bypassing normal steps that include checking SPF, DKIM and DMARC.
Source: SEC Consult
In the image above, you’ll note the initial short email with the email body of “lorem ipsum.” But then there’s this extra email with the email body of “I am the admin now!” The specific content is irrelevant (other than to provide an example of something benign vs. malicious in nature), but it shows how SMTP smuggling occurs.
According to Longin, this method can be used to impersonate emails from any high-profile brand. This is where it becomes a real problem. Users that have not undergone security awareness training will be more prone to believing an email is actually from the company it claims to be, falling for the socially-engineered scam within.
The vulnerability was initially reported to vendors in late July. Microsoft has since rolled out a patch, but other vendors, including Cisco, have yet to do so.
KnowBe4 enables your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
 Here's how it works:
Here's how it works:




