Scammers are shifting to SMS to carry out business email compromise (BEC) attacks, since text messaging offers less visibility to the victim and more flexibility to the attacker, says James Linton at Agari.
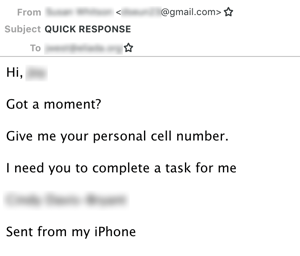
BEC attacks have traditionally centered around email exchanges, although phone calls and text messages can play a role. Agari has observed a recent trend, however, in which attackers send an initial email requesting the victim’s phone number, and the rest of the scam takes place via text message.
“By moving them over to their cell phone, the scammer is equipping their victim with all the functionality needed to complete the task that is to be given to them,” writes Linton. “A mobile device offers instant and direct messaging, the ability (in most cases) to still access email, the ability to take pictures with the phone’s camera, and far greater portability than a laptop, which all increases the chances that the scammer will be successful in achieving their desired outcome once a victim is on the hook.”
As an example, Linton points to a scammer group tracked by Agari that impersonates the targeted organization’s CEO, and then attempts to trick an employee of that organization into buying gift cards and sending photos of the codes to the attacker.
“In a mobile BEC scam, the actor has the ability to play a greater role in guiding the victim throughout the entire gift card buying process,” he says. “SMS is more conversational in nature than email, which mitigates potential stumbling blocks in the completion of the task.”
While SMS-based phishing, or smishing, is nothing new, attackers are increasingly starting to see the advantages of SMS for more elaborate scams. And think about your policies, too. If your C-suite is in the habit of having employees make large-scale purchases of gift cards on the company dime, maybe you should rethink that. New-school security awareness training can help your employees keep up with the constantly evolving tactics used by attackers.
 Here's how it works:
Here's how it works:




