 Analysis of a new initial access malware attack shows how simple these attacks can be while also proving that malware can reside on legitimate repositories.
Analysis of a new initial access malware attack shows how simple these attacks can be while also proving that malware can reside on legitimate repositories.
Security analysts at cybersecurity company Fortinet dissect the methods and actions taken by a new malicious Java-based downloader intent on spreading the remote access trojans (RAT) VCURMS and STRRAT.
According to the analysis, the threat actors store their malware on public services that include Amazon Web Services (AWS) and GitHub, using the commercially-available code obfuscator Branchlock to avoid detection of the malicious Java code.
The start of this attack is little more than a “Remittance Summary” email that includes what appears to be a PDF attachment, but is actually an image linking to the malicious java file:
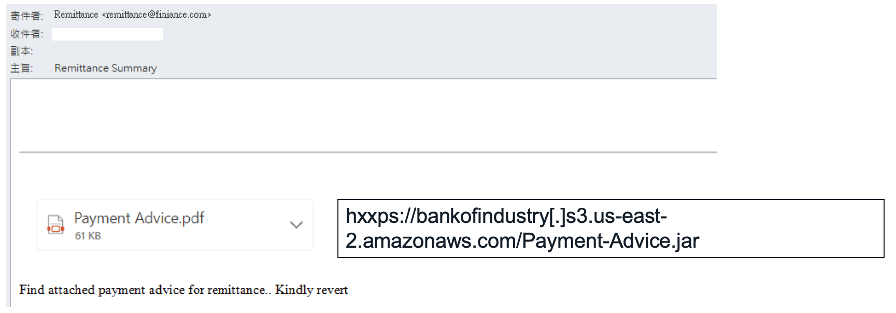
Source: Fortinet
The final payload includes a keylogger, password recovery malware and one of the two RATs.
I spend a lot of time covering rather sophisticated campaigns; this one is the complete opposite: just click the “attachment” and let the Java do the rest. That’s it — just one click and the rest is done.
This attack demonstrates just how simple phishing can be to find its next victim. The use of legitimate services and obfuscation of malicious code make it difficult for security solutions to spot the email as being malicious. This leaves only the user who has undergone continual security awareness training to quickly realize that this email is bogus and to promptly delete it. To do anything else is to ensure a RAT in your proverbial kitchen.
KnowBe4 empowers your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
 Here's how it works:
Here's how it works:




