 The mysterious Shadow Brokers – the hackers who leaked the NSA SMB zero-day exploit that powered WanaCry into the world's worst ransomworm – are back, and could cause even more damage.
The mysterious Shadow Brokers – the hackers who leaked the NSA SMB zero-day exploit that powered WanaCry into the world's worst ransomworm – are back, and could cause even more damage.In their purposely scrambled English – to evade language analysis and getting caught – Shadow Brokers published a new manifesto, announcing a fresh subscription offer starting June 2017 where they will release more zero-day bugs and exploits for various desktop and mobile platforms, stolen from the NSA.
This time though, Shadow Brokers attack code will only be available for limited parties willing to pay. Here is a snippet:
Wine Of The Month Club
"TheShadowBrokers (TSB) is launching new monthly subscription model. Is being like [the] wine of month club. Each month peoples can be paying membership fee, then getting members only data dump each month."
The problem is that now bad guys will subscribe to the TSB service, and have time to use these exploits before patches come out. A recipe for disaster.
Who would be possible other TSB "customers"? Other state-sponsored hackers like Russia and China, working through proxies, large media organizations and software companies, and IT security companies to name a few.
TSB Subscribers Get Exclusive Access
Someone subscribing to the TSB SaaS would get exclusive access to any of their carefully chosen leaks, which they claim might include:
- Exploits for operating systems, including Windows 10.
- Compromised data from banks and Swift providers.
- Exploits for web browsers, routers, and smartphones:
- Stolen network information from Russian, Chinese, Iranian, and North Korean nuclear missile programs.
Their claims seem legit. Their last dump was the real deal, the goods were what they claimed they were, and caused worldwide chaos when integrated in the WanaCry ransomware.
Before publicly dumping these exploits in April, the Shadow Brokers put an auction of cyber weapons stolen from NSA’s elite hacking team called Equation Group for 1 Million Bitcoin.
After failed auction, the hacking group even put up those hacking tools and exploits for direct sale on an underground site, categorizing them into a type — like "exploits," "Trojans," and "implant" — each of which ranged from 1 to 100 Bitcoins (from $780 to $78,000).
After failure from all sides, the group started leaking those hacking exploits. Last month, the Shadow Brokers released a Microsoft Windows SMB exploit that was used by the WannaCry ransomware, which infected 200,000 machines in 150 countries within just 48 hours.
When TSB discussed possible WannaCry ties with the North Korean state-sponsored hacking group Lazarus Group, they stated:
"The Oracle is telling the shadow brokers North Korea is being responsible for the global cyber attack Wanna Cry. Nukes and cyber attacks, America has to go to war, no other choices!", and then lashed out against the US government and tech companies for not buying and fixing the exploits when they had the chance.
How vulnerable is your network against ransomware infections?
Bad guys are constantly coming out with new versions of ransomware strains to evade detection. Is your network effective in blocking ransomware when employees fall for social engineering attacks?
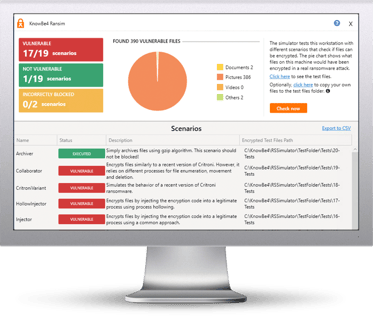
KnowBe4’s Ransomware Simulator "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 ransomware infection scenarios and show you if a workstation is vulnerable to infection.
Here's how RanSim works:
![]() 100% harmless simulation of a real ransomware infection
100% harmless simulation of a real ransomware infection![]() Does not use any of your own files
Does not use any of your own files![]() Tests 10 types of infection scenarios
Tests 10 types of infection scenarios![]() Just download the install and run it
Just download the install and run it ![]() Results in a few minutes!
Results in a few minutes!
Download RanSim Here:
https://www.knowbe4.com/ransomware-simulator
NOTE: Created for Windows-based workstations running Windows 7+. RanSim does not alter any existing files on disk. As part of the simulation RanSim does enumerate all files on the local disk(s). For the purposes of encryption, simulated data files are downloaded from the Internet.




