 Data breaches continue, phishing attacks are on the rise, and people responsible for security wake up in a cold sweat a few times a year worried they’re the next victims.
Data breaches continue, phishing attacks are on the rise, and people responsible for security wake up in a cold sweat a few times a year worried they’re the next victims.
The industry probably won’t be able to agree what “fixing” security actually means, but that doesn’t mean we can’t take steps to optimize security. Often times, in the aftermath of a breach, we find that it’s not the lack of tools or information that contributed to the event, but rather the available resources were not deployed appropriately.
While there is no one size fits all approach, here are seven tips you can use to optimize security today.
- Start with why
Unless you’re running a security business, chances are security is just a function to support the business. Therefore, it is crucial to understand what the business is, what actually makes the money, and therefore what needs to be protected.
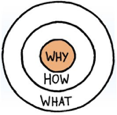
Professionals understand what security is, how security is done, but do they really understand why?
A CIO at a drinks company was once asked what his job was, his response was, “My job is to help the company sell more beer.”
Think about what your security function is doing and whether it’s helping your company sell more beer.
To understand the concept better, it’s useful to watch this TED talk by Simon Sinek.
If we know why – then the how and the what become clearer.
- Focus on the root cause
Among all the different technologies, and methods to solve different threats, it can be easy to overlook the simple fact of looking at the root cause. That means to look at the initial penetration bad actors use to get into the organization.
For example, phishing is a root cause – it can lead to ransomware, other malware, CEO fraud, third-party fraud, among others. By focusing on this as a root cause, many potential threats can be addressed.
Complexity is the enemy here, and a silent contributor to many breaches owing to the fact that it hides the root cause and obscures which controls should be put in place. Simplifying systems is not an easy task – and neither is it one that the security team can do in isolation from the organization.
But simplifying the security estate is a good starting point. Simply having more tools isn’t the answer, and more data is useless without the ability to make sense of it.
- Manage alerts
As attacks increase, from both external and internal sources, it is inevitable that things will slip past preventative controls – therefore threat detection controls need to be put in place. But even in medium-sized enterprises, the number of alerts being generated across multiple systems can quickly become overwhelming.
While it can be tempting to invest a lot into correlating all the logs and wading through the alerts, the alternative is to understand the organisational systems and only turn on alerts for critical activities and systems. This ties back into understanding root causes and simplifying the overall architecture. Having fewer, but more focussed and better-quality alerts can allow organisations to spend more time focussing on the things that really matter.
Honeytokens can help to reduce noise in the environment. When implemented correctly, alerts generated by honeytokens are of high quality and can pinpoint malicious activity.
Good system architecture can also help in managing and reducing alerts. For example, designing simple communication flows between components can help identify where traffic is behaving in a non-standard way – such as lateral movement by hackers within your system.
- Leverage the community
Having limited resources doesn’t necessarily mean resigning yourself to making do. There is a plethora of resources available that can help you maximise the benefit.
For example, not having a training budget doesn’t mean your staff can’t get trained. YouTube videos and blogs exist that can be accessed for free (or nearly free) on a variety of topics. Alternatively, attending conferences and events can help increase your team’s knowledge.
Many publicly available standards and best practice documents also exist – saving you the time and effort needed to create them yourself.
Finally, a wide array of open source tools are available that can be tailored to meet your organization’s specific needs.
- Start marketing
User education such as security awareness training and gaining stakeholder support are common challenges that many security departments face. One of the reasons for this is that security departments often try to either sell security or scare people into compliance.

However, marketing is another way. By marketing security, the intended message can be delivered to the intended audience in a far more impactful way that creates behavioural change over time. Changing behaviours is the key to improving the efficiency of security within an organization. The better buy-in users and stakeholders have, the less likely they will oppose security initiatives, fall victim to scams or undertake behaviour that undermines security.
Check out some of the wide range of resources available at KnowBe4.
- Reduce the impact
When it comes to security, optimizing the day-to-day operations is only part of the battle. The real challenges occur when an incident occurs.
Seatbelts, airbags and crumple zones in vehicles don’t stop an accident, but can reduce the impact and increase the chances of passenger survival.
Similarly, security teams can put in place controls and measures to reduce the impact of a breach. For example, architecting systems in a segmented manner can minimize the amount of data a would-be attacker can get hold of.
Similarly, critical components should be designed with tolerance in place, so that they can be rebuilt quickly and frequently.
Upfront planning can help make it easier to recover following a compromise. Laying out a communication plan with employees, partners, shareholders and customers prior to an event can help mistakes being made in the heat of an incident.
- Assurance
Once all security systems, technologies, and processes have been put in place, it is vital they are tested in order to gain assurance they are working as designed. Penetration testing, or red-team exercises, are common practice amongst large enterprises.
In addition to these, smaller tests can be undertaken, often in-house to check the effectiveness of controls. Copying large amounts of data onto removable media, connecting from non-corporate devices, or incorrectly guessing login details can be easy ways to test if security is operating as intended.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




