 Security awareness training (SAT) works! A well-designed security awareness training campaign will significantly reduce cybersecurity risk.
Security awareness training (SAT) works! A well-designed security awareness training campaign will significantly reduce cybersecurity risk.
We can safely state that from over 13 years of experience with tens of thousands of customer organizations and hundreds of millions of customer interactions. We have the data to prove it.
The average new customer comes to us with about a third of their workforce proven to click on any
phishing email. After training and simulated phishing tests, that rate drops down to around 5% in a year
or less (as summarized by the graphic below).
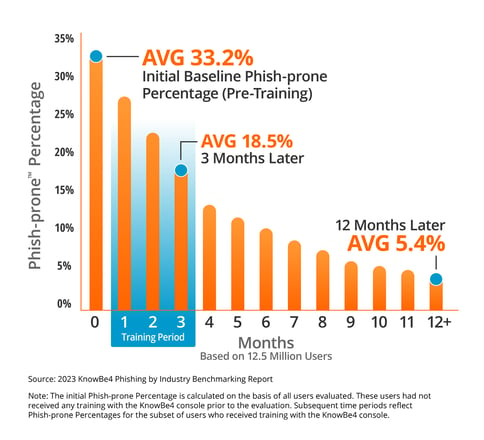
These are not only our best customers. It is an average of all customers, whether they follow our best
practices or not. We have many customers with click rates down below 2%.
100% Effectiveness Requirement Questioned
Some critics say that because SAT is not 100% effective in reducing risk and that at least some
employees will always click on any phish, it is not worthwhile. We do wonder why SAT is the only
security control held to the 100% effectiveness standard. No other security control has to be 100%
effective in order to be recommended. For example, patching is rarely 100% accomplished across any
organization, but everyone still recommends patching. Antivirus programs are notorious for missing
malware, but no one would say you could do without it.
SAT is reducing social engineering risk from around one-third to about 5% or less. That is a HUGE
reduction in cybersecurity risk and one that any other cybersecurity control would be glad to have.
Cybersecurity defense is all about risk reduction (not elimination) and SAT significantly reduces risk.
Technical Defenses Only
Some defenders strongly support technical defense-only solutions (e.g., content filtering, antivirus, etc.)
and say that as soon as technical defenses block 100% of phishing, SAT will not be needed. That is
perhaps true, but there are two problems. The first is that no one has come close to creating a technical
defense that is 100% accurate at detecting and blocking social engineering and phishing. This is despite
vendors trying for decades and spending billions of dollars. Phishing detection rates have improved
slightly for some vendors over time, but all still allow some non-minor amount of social engineering and
phishing to get to end users, and long as that is true, SAT will be needed.
Second, most people imagining a world where a technical defense can prevent 100% of phishing are
only considering email phishing…and maybe web-based phishing. There are many other ways social
engineering and phishing can interact with an end user, including SMS, social media, voice calls, QR
codes, and communication apps (like WhatsApp, Slack, Microsoft Teams, etc.). There is not a technical
defense that would cover all these avenues, especially with end-to-end (E2E) encryption growing in
popularity.
There are many forms of social engineering and phishing that do not seem well-suited for defeat by
technical defenses, including call-back phishing. Call-back phishing usually displays a long-distance
number for the potential victim to call. The technical defense would have to be able to call the number,
interview the call center employee, and then make a determination as to its intent and validity. Call
center phone numbers come and go with nearly as much frequency as temporary websites and email
addresses.
Many types of social engineering and phishing, such as romance and employment scams, would be hard
for a corporate technical defense to detect and prevent. In most of these cases, the contact with the
victim is usually made using their personal accounts and the employee is often not involving or actively
hiding the communication from the employer. But a little employee education can go a long way in
preventing an employee from becoming yet another victim.
Long-term spear phishing attacks, where the attacker has established a previous relationship, often with
the victim using their personal accounts, are going to be difficult for a corporate technical solution to
detect. Oftentimes, the majority of the communication does not involve any noticeable malicious
content, file, or link, until the ultimate trap is sprung. Even then the language used is very customized by
the attacker for the particular situation and scam.
AI and Deepfakes
Yes, AI and deepfakes will make some phishing attacks more realistic, but every phishing attack has signs
that it is a phishing attack, and that is why good, effective SAT is needed more than ever. Users need to
be trained to spot, mitigate, and appropriately report attacks, no matter how realistic they may look.
That takes more training, not less.
Most critics are making statements after short-term studies or only limited experience with one or a few
projects. We have data from over 65,000 customers and hundreds of millions of simulated phishing
tests. The data consistently shows that the more frequently employees are trained, the better they are
at spotting phishing attacks.
SAT is education. When has more and better education not been part of a solution to any problem? Why
would cybersecurity, social engineering, and phishing be any different? We are not speculating. We have
the data to prove that a good, effective security awareness training program is one of the single best
things any organization can do to reduce cybersecurity risk.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




