 Atlanta-based SecureWorks has a Counter Threat Unit which has been closely watching the Russian hacker gang APT28 over the last few years and released brand new research. This group of criminal hackers is also known as Pawn Storm, Sofacy, Strontium, Fancy Bear, and SecureWorks calls them "IRON TWILIGHT".
Atlanta-based SecureWorks has a Counter Threat Unit which has been closely watching the Russian hacker gang APT28 over the last few years and released brand new research. This group of criminal hackers is also known as Pawn Storm, Sofacy, Strontium, Fancy Bear, and SecureWorks calls them "IRON TWILIGHT".
Their researchers state it is highly likely they are supported by the Russian Government, specifically the GRU which is the Russian military intelligence arm, the counterpart of the FSB (former KGB). APT28 "active measures" were trying to influence U.S. presidential elections and at the moment try to do the same thing in France and Germany.
APT28 moves from just spying to sabotage
SecureWorks said: "The threat group has targeted non-governmental organizations (NGOs), journalists, politicians, political organizations, governments, and militaries since at least 2009. SecureWorks® Counter Threat Unit™ (CTU) researchers assess it is highly likely that IRON TWILIGHT is sponsored by the Russian government. In Spring 2015, the Russian government began tasking IRON TWILIGHT with activity beyond covert intelligence gathering. The group conducted a sabotage operation against France-based TV station TV5Monde and leaked political details in what U.S. intelligence agencies concluded was an attempt to influence the U.S. presidential election."
"Prior to 2015, IRON TWILIGH targets were consistent with a government intelligence agency tasked with covertly gathering military intelligence. In 2015, there were reports that IRON TWILIGHT had performed credential spear phishing attacks against Russian political activists, bloggers, and politicians; had targeted U.S. journalists; and had compromised the network of the German Bundestag parliament."
Attack vectors: phishing emails and drive-by downloads at scale
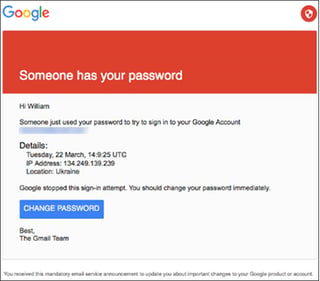
Since March 2015, the group has attacked thousands of Gmail users using phishing attacks to steal credentials. IRON TWILIGHT has used spear phishing emails with malicious document attachments or links to a custom exploit kit. Its toolset includes malware for Windows, Mac OS X, and Linux-based operating systems and mobile devices. The threat actors also use targeted phishing campaigns to steal webmail credentials. As IRON TWILIGHT operates this capability at scale, automation likely accesses and exfiltrates data from compromised accounts.
IRON TWILIGHT's hacking toolkit
- Exploit Kits, one for spear phishing campaigns and strategic web compromises. The other one as malware via an attachment to a spearphishing email.
- First Stage Malware like the Carberp trojan to establish access to a target environment, perform reconnaissance, and facilitate installation of second-stage tools.
- Second Stage Tools like the XAgent modular remote access trojan (RAT) and the XTunnel persistent backchannel tool. XAgent can jump air-gapped networks by infecting USB storage devices and can be used against Windows and Unix-based operating systems.
- Endpoint Tools like a kit named Scaramouche that consists of screen capture and credential theft tools.
What to do about It
SecureWorks recommends the following excellent best practices to prevent network compromise:
- Apply best-practice security controls such as regular vulnerability scanning and patching,
- Have network monitoring tools in place.
- User education reduces your susceptibility to compromise.
- Implement two-factor authentication (2FA) on internal and third-party webmail platforms.
- Encourage employees use 2FA on their personal accounts.
- Restrict work-related communication from personal email.
If you want to spend less time putting out fires, get more time to be proactive, and get the things done you know need to be done, step your employees through effective security awareness training. It will help you prevent compromises like this or at least make it much harder for the bad guys to social engineer your users.
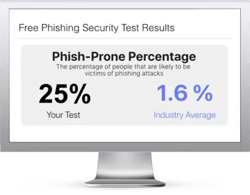
Free Phishing Security Test
Would your users fall for CEO Fraud and other social engineering attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
 Here's how it works:
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





