 A sophisticated phishing attack is trying to get confidential corporate information. Bad guys are sending spoofed emails claiming to be from the Security and Exchange Commission, and target lawyers, compliance managers, and the very company officials who file documents with the SEC.
A sophisticated phishing attack is trying to get confidential corporate information. Bad guys are sending spoofed emails claiming to be from the Security and Exchange Commission, and target lawyers, compliance managers, and the very company officials who file documents with the SEC.
Late February 2017, FireEye identified this spear phishing campaign based on multiple similar tools, tactics, and procedures, and have high confidence that this campaign is associated with the financially motivated threat group tracked by FireEye as FIN7.
FIN7 is a financially motivated intrusion set that selectively targets victims and uses spear phishing to distribute its malware. FireEye have observed FIN7 attempt to compromise diverse organizations for malicious operations – usually involving the deployment of point-of-sale malware – primarily against the retail and hospitality industries.
Spear Phishing Campaign
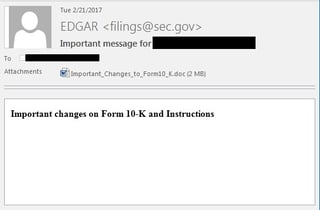
All of the observed intended recipients of the spear phishing campaign appeared to be involved with SEC filings for their respective organizations. Many of the recipients were even listed in their company’s SEC filings. The sender email address was spoofed as EDGAR <filings@sec.gov>, the attachment is named “Important_Changes_to_Form10_K.doc”.
Victims
Thus far, FireEye directly identified 11 targeted organizations in the following sectors:
- Financial services, with different victims having insurance, investment, card services, and loan focuses
- Transportation
- Retail
- Education
- IT services
- Electronics
All these organizations are based in the United States, and many have international presences. As the SEC is a U.S. regulatory organization, we would expect recipients of these spear phishing attempts to either work for U.S.-based organizations or be U.S.-based representatives of organizations located elsewhere. However, it is possible that the attackers could perform similar activity mimicking other regulatory organizations in other countries.
First International Cybermafia
John Miller, a director of threat intelligence at FireEye, described the attackers as among "the most sophisticated financial actors" and said their methods were similar to hackers who targeted ATM machines and other parts of the banking system. He also warned the hacking tools they sought to install were particularly insidious.
“It's the Swiss army knife of malware. It lets you do whatever you want to with the compromised system," Miller said. Fin7 is the first international cybermafia, a group of cybercriminals from Russia, Ukraine and other parts of Europe and China.
Are you aware that many of the email addresses of your organization are exposed on the Internet and easy to find for cybercriminals? With these addresses they can launch social engineering, spear-phishing and ransomware attacks on your organization. The Email Exposure Check (EEC) is a one-time free service. Sign up for your free EEC and find out now which of your email addresses are exposed.

Don't like to click on redirected buttons? Cut & Paste this in your browser:




