 Cisco has a separate threat research group called Talos. They just published a report on a scary new form of malware that’s hard to detect.
Cisco has a separate threat research group called Talos. They just published a report on a scary new form of malware that’s hard to detect.
They called it DNSMessenger, and the malicous code uses Microsoft PowerShell scripts to hide itself in memory and connect directly with a command & control server using the compromised machine's Domain Name Service port.
It’s distributed through a phishing campaign with a Microsoft Word document attached, trying to look like a known or reputable source.
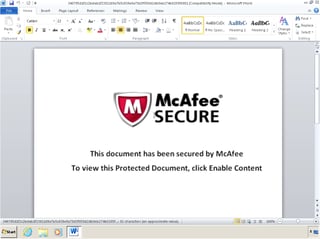
Once the user opens the file, it pretends to be a protected document secured by McAfee Security and asks the user to once again click to view the content that was supposedly in the original file. As you guessed, the file has no content and the second click instead executes the malicious script hidden in the file, leading to the workstation being compromised.
Here is the new angle that makes it hard to detect. The malicious code does everything in memory, and the second stage is stored in the Alternate Data Stream with the NTFS (standard Windows) file system or directly inside the registry, while a third-stage PowerShell script establishes communications with a command-and-control server via DNS that is used to pass text messages. Normally, HTTP and HTTPS gateways are monitored by security software, but that's not always the case for DNS, and the hackers know it.
Talos could not yet immediately see what commands are going back and forth: “We were unable to get the C2 (command and control) infrastructure to issue us commands during our testing,” the Talos team said in a blog post Thursday. “Given the targeted nature of this attack, it is likely that the attackers would only issue active C2 commands to their intended target.”
“This malware sample is a great example of the length attackers are willing to go to stay undetected while operating within the environments that they are targeting,” the Talos team added. “It also illustrates the importance that in addition to inspecting and filtering network protocols such as HTTP/HTTPS, SMTP/POP3, etc. DNS traffic within corporate networks should also be considered a channel that an attacker can use to implement a fully functional, bidirectional C2 infrastructure.”
Preventing Malware Infections
Which user will infect your network malware? We've got something really cool for you: the new Phishing Security Test v2.0!
It's got several great new features, and sending simulated phishing emails to train your employees is a fun and an effective best practice to patch your last line of defense... your users.
The phish-prone percentage is usually higher than you expect and is great ammo to get budget. You can now find out the current Phish-prone percentage of your organization and who might infect your network with ransomware.
With Our Brand-New Phishing Test:
- You can customize the phishing test based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- Already did a phishing test in the past? For a limited time you can reset it yourself and do a new one.
Start phishing your users now. Fill out the form, and get started immediately. There is no cost.
Don't like to click on redirected buttons? Copy and paste this link in your browser:
https://info.knowbe4.com/phishing-security-test-kmb
Let's stay safe out there.
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc

(*) Allow 4-6 weeks for delivery.





