 It appears the holidays aren’t without a cyber-grinch, as attackers use the lure of free money in the form of a gift card as an easy means to trick victims into infecting their own computers.
It appears the holidays aren’t without a cyber-grinch, as attackers use the lure of free money in the form of a gift card as an easy means to trick victims into infecting their own computers.
According to security researchers at the Cybereason Nocturnus Team, this scam takes advantage of the holiday season and victim’s desire to have a little more in their wallet to spend on gifts – delivering a nasty present on the tail end: the Dridex Trojan. Dridex is nasty stuff; it’s responsible for exfiltrating both credentials and data from a victim organization. It’s the very definition of malware you don’t want installed on your network.
The attack begins with a simple enough phishing campaign impersonating Amazon using realistic-looking icons, images, sender’s email address, etc. informing the recipient that Amazon (out of the kindness of Jeff Bezos’ heart) is simply giving away $100 as their way of “saying thank you.” (this is the first red flag)
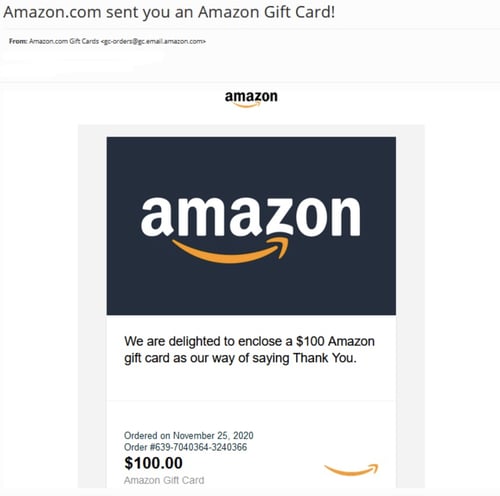
The user is prompted to download the gift card (the second red flag). The file downloaded is either a macro-infested Word doc, a screensaver file (.SCR), or a visual basic script file (.VBS) each using a filename similar to “Amazon_eGift_Card.<gift card number posted in the email>”
You can’t afford to allow scams like this to succeed; especially at a time of year when emotions are running high, excitement is in the air, and people’s defenses are down. But the same is true as we move into 2021 – the bad guys will simply find the next reason to offer up another gift card, making this attack useful anytime of the year.
Teach your users to avoid becoming a victim to these obviously “too good to be true” scams with Security Awareness Training that provides your users with educational content on why being vigilant is important to the organization, what they should be looking out for, and what steps to take (and not take) when encountering an email they believe to be part of a phishing attack.
 Here's how it works:
Here's how it works:




