 You probably remember the 2012 LinkedIn data breach. It was a big deal because something like 6.5 million user account passwords were posted online, but LinkedIn never confirmed the final number of people that were impacted.
You probably remember the 2012 LinkedIn data breach. It was a big deal because something like 6.5 million user account passwords were posted online, but LinkedIn never confirmed the final number of people that were impacted.
Well, it turns out that really 117 million records were stolen which have both emails and passwords that were easily decrypted. And this new number is all over the news because that database is now sold on the dark net. It is not unusual for such stolen material to turn up for sale long after the initial data breach.
LinkedIn is invalidating the compromised passwords and currently sending out emails to users, urging them to change their passwords in response to this report (though the email LinkedIn is sending is vague about the actual nature of the threat).
And of course the bad guys have jumped on this too. It's prime time for them to exploit user fear and confusion and send out their own fake versions of that email, and other LinkedIn-themed phishing attacks. That means you need to inoculate your users before they fall for these new scams. I suggest you send employees the following. Feel free to copy/paste/edit:
"The original LinkedIn 2012 databreach turns out to have been much larger than the estimated 6.5 million username and passwords that were stolen. There are really more than 100 million records compromised and LinkedIn is sending emails to these users that they need to change their password.
The bad guys however, are jumping on this as well and are sending phishing emails with a fake LinkedIn login page. If you fall for this scam and log in on their fake page, your credentials will be stolen and your LinkedIn account compromised and/or your computer infected with all kinds of malware.
If you receive an email that seems to come from LinkedIn, hover over the links and make sure they are legit before you click. Even better, do not click on anything and just go to LinkedIn using your browser and change your password. If you have used your LinkedIn password for other sites, it's time to change those as well!"
Go to www.LinkedIn.com, click Help, (bottom right) and choose Changing Your Password. In case you want to get another layer of password protection, LinkedIn also offers dual factor authentication by which you can have a one time numerical code sent to your smartphone each time you need to access your LinkedIn account.
The number of compromised records is very close to the number of active LinkedIn users in 2012, meaning the breach likely affected all users at the time. They should have forced every user to change their passwords back then, instead this sensitive data has been floating around for the last 4 years. Users that haven't changed their password in that time frame are unsurprisingly the same type of user that has the same password for multipla accounts aka a hacker's paradise. Yet another reason why password security is so vital in protecting our identities online.
Data breaches like this make tactics like social engineering even easier for cybercriminals by exposing information that should never become public. It also opens up a user base like LinkedIn's to even more threats.
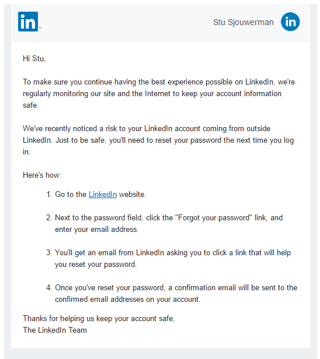
For KnowBe4 customers, we have added a new template in the Current Events section. It is very close to the original LinkedIn email, so it has a 4-star difficulty rating. The subject is "Reset your LinkedIn Password".
PS: If you are not a KnowBe4 customer yet, send a (no-charge) Phishing Security Test to your users and find out the Phish-prone percentage of your employees. The results are often shocking but a good way to get budget. Start here:
PS, don't like to click on redirected buttons? Cut & Paste this in your browser:
https://www.knowbe4.com/phishing-security-test-offer





