OK, this is a heads-up about a new aggressive form of email attack that you need to warn your employees, friends and family about. The bad guys have beta-tested and refined it in Australia, and now the first incidents have been spotted in the US.
The sophisticated attackers are targeting potential victims in an email sequence that starts with pornography and adult dating links, which are then followed up with extortion attempts.
IT security company Forcepoint says it picked up more than 33,500 such emails in August, and Australian email addresses were used to test the criminal campaign.
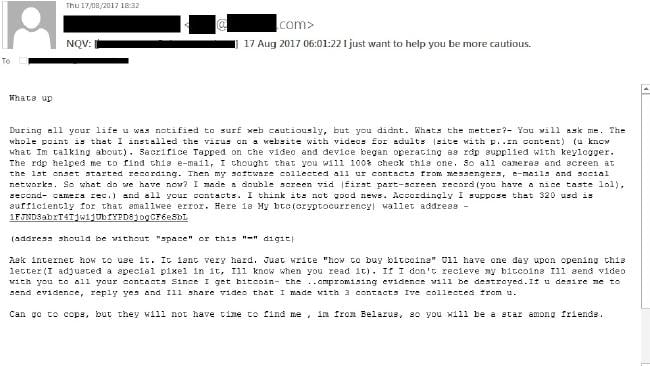
The scam threatens to steal users’ privacy, sequencing emails that say, “look at this”, then “we know what you just looked at”, and demand $US 320 payment in Bitcoin.
The email claims that a virus was installed on a porn website which recorded the victim through their webcam. “Then my software collected all your contacts from messengers, e-mails and social networks,” it says. “If I don’t receive my Bitcoins I’ll send video with you to all your contacts.”
Carl Leonard, principal security analyst at Forcepoint, said cyber-extortion was a prevalent tactic today. While it largely takes the form of ransomware, he said data exposure threats were growing in popularity.
“Cyber-blackmailing continues to prove as an effective tactic for cybercriminals to cash out on their malicious operations,” he said. “In this case, it appears that a threat actor group originally involved in adult dating scams have expanded their operations to cyber-extortion campaigns as a result of this trend.”
Company Email Addresses Specifically Targeted
Leonard said company email addresses were specifically targeted, which would have added additional pressure to potential victims “since it implies that a recipient’s work PC was infected and may therefore taint one’s professional image”. “It is important for users to verify claims from the internet before acting on them,” he said. “Most online attacks today require a user’s mistake before actually becoming a threat. This is something that can be mitigated by addressing the weakness of the human point.” We agree.
But Leonard said the scale of this campaign suggested the scammers were bluffing about having compromising information. "If the actors did indeed possess personal details of the recipients, it seems likely they would have included elements [such as name, address or date of birth] in more targeted threat emails in order to increase their credibility.
"This led us to believe that these are simply fake extortion emails. We ended up calling it ‘fake-tortion’.”
I suggest you send the following to your employees, friends, and family. You're welcome to copy, paste, and/or edit:
"There is a new, sophisticated email scam you need to watch out for. Bad guys first send emails with links to inappropriate websites to business email addresses, and then follow up with extortion threats, claiming your workstation is infected and that they "know what you just looked at", and say they will send a video to all your email contacts, because they "recorded what you were watching".
If this type of scam email makes it through the spam filters into your inbox, do not click on any links, do not reply, and delete the message (or click on the Phish Alert button). Do not download any software to check your computer for viruses, but follow procedure to report these types of criminal emails. Remember: Think Before You Click." It is more important than ever these days."
If you are a KnowBe4 customer, inoculate your users against this. In your console, go to Go to: Phishing->Email Templates->System Templates->Controversial->I just want to help you be more cautious. You will see a ready-made, 4-star rated template. You can get a campaign out to all users in less than 2 minutes.
Let's stay safe out there.
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc.

What is your actual social engineering attack surface?
We have something super cool for everyone, customers and non-customers both, and there is no cost.
Many of the emails addresses and identities of your organization are exposed on the Internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization.
Our NEW Email Exposure Check Pro goes even further to identify the at-risk users in your organization by crawling business social media information and scouring hundreds of breach databases. This is done in two stages:
First Stage: Does deep web searches to find any publicly available organizational data. This will show you what your organizational structure looks like to an attacker, which they can use to craft targeted spear phishing attacks.
Second Stage: Finds any users that have had their account information exposed in any of several hundred breaches, using Have I Been Pwned. These users are particularly at-risk because an attacker knows more about that user, up to and including their actual passwords!
Your EEC Pro Reports: We will email you back a summary report PDF of the number of exposed emails, identities and risk levels found. You will also get a link to the full detailed report of actual users found, including breach name and if a password was exposed.
This is so important that even if you already ran your one-time no-charge legacy EEC, you are eligible to try the new Pro version. Run your complimentary one-time Email Exposure Check Pro here. Results come back in a few minutes:
PS: Don't like to click on redirected buttons? Copy/Paste this in your browser:
https://info.knowbe4.com/email-exposure-check-pro-chn





