 Michael Kan at PC Mag reported: "According to the FBI, Egor Igorevich Kriuchkov promised to pay as much as $1 million to the employee to help his shadowy group steal data from a Nevada-based company for ransom purposes.
Michael Kan at PC Mag reported: "According to the FBI, Egor Igorevich Kriuchkov promised to pay as much as $1 million to the employee to help his shadowy group steal data from a Nevada-based company for ransom purposes.
The FBI has arrested a Russian citizen for trying to recruit an employee of an unnamed Nevada-based company to plant malware inside the firm.
According to the US Justice Department, 27-year-old Egor Igorevich Kriuchkov promised to pay as much as $1 million to the employee. The goal: to steal data from the company and then threaten to make the information public, unless a large ransom was paid.
The scheme was expected to fetch $4 million from the victim company. However, the Justice Department’s complaint suggests the employee ended up secretly working with the FBI to gather evidence against Kriuchkov, who was arrested on Saturday in Los Angeles.
Kriuchkov first made contact with the employee on July 16 via WhatsApp through a mutual acquaintance. Kriuchkov then flew from Russia to the US to travel with the employee for a trip to Lake Tahoe. On Aug. 3, the Russian national revealed his true reason for meeting up, saying he worked for a “group” that specializes in exhorting companies.
“Kriuchkov went on to explain that the 'group' pays employees of target companies to introduce malware into the target company’s computer system,” the FBI’s complaint says. “Kriuchkov said the ‘group’ has performed these ‘special projects’ successfully on multiple occasions, and identified some of the targeted companies.”
As for the malware, Kriuchkov told the employee it was designed to first create a ruse through a DDOS-like disruption in the victim’s corporate network. However, the real primary attack would loot data from the company's databases and send it back to the group Kriuchkov was working for.
Initially, Kriuchkov was going to pay the employee $500,000 through Bitcoin or cash. But then he agreed to pay $1 million after the employee demanded more.
“To ease [the victim employees’] concerns about getting caught, Kriuchkov claimed the oldest ‘project’ the ‘group’ had worked on took place three and a half years ago and the ‘group’s’ co-optee still worked for the company,” the FBI’s complaint says.
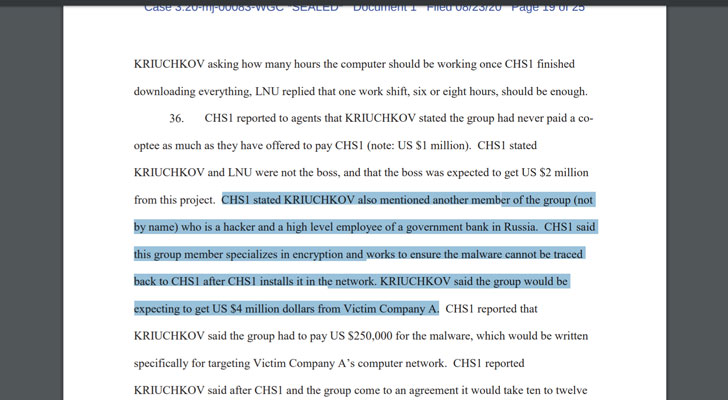
Whether Kriuchkov has any ties to the Russian government was left unsaid. But according to the complaint, he worked with a hacker who was also a “high-level employee of a government bank in Russia.”
Kriuchkov was working to plant the malware inside the Nevada company possibly this month before his shadowy group decided to delay the project. During that time, the FBI gathered evidence against him partly by monitoring his meetings with the employee.
“In this matter, the FBI was once again able to intervene before any damage could occur,” said Aaron Rouse, FBI special agent in charge of the Las Vegas division, in today’s announcement.
On Monday, Kriuchkov made his first appearance before a federal court. He now faces a statutory maximum sentence of five years in prison and a $250,000 fine."
This begs the question how many other high-profile ransomware and data breach attacks might have been executed in the same way by bribing an insider.
Cross-posted with grateful acknowledgement to PC Mag.
 Here's how it works:
Here's how it works:




