 By Eric Howes, KnowBe4 Principal Lab Researcher. Well over a year ago we reported on the rise of a new form of CEO fraud in which malicious actors persuaded unwitting employees working in the payroll departments of targeted organizations to change the direct deposit information for senior executives to point to bank accounts controlled by said malicious actors. Since then, direct deposit (or payroll) phishing has gotten the attention of the mainstream news media and become one of the most common forms of CEO fraud that we see day in and day out.
By Eric Howes, KnowBe4 Principal Lab Researcher. Well over a year ago we reported on the rise of a new form of CEO fraud in which malicious actors persuaded unwitting employees working in the payroll departments of targeted organizations to change the direct deposit information for senior executives to point to bank accounts controlled by said malicious actors. Since then, direct deposit (or payroll) phishing has gotten the attention of the mainstream news media and become one of the most common forms of CEO fraud that we see day in and day out.
As we noted at the time, these phishing campaigns demonstrated that "the bad guys are more than capable of learning and adapting from previous experiences dealing with employees in these kinds of CEO Fraud operations." Indeed, that's something we have stressed repeatedly in this space -- that the malicious actors who prosecute these kinds of attacks are always learning, always adapting, and always working to take their game to the next level.
A few days ago we spotted a direct deposit phish that had managed to hook an unsuspecting employee, resulting in an exchange of emails and attachments. The employee in this case ultimately wised up and hit the Phish Alert Button (PAB), reporting the entire incident to us as well as her organization's IT department.
What caught our eye, though, was how much more practiced and comfortable the bad guys had become in executing this kind of attack since last year. Let's take a look.
The Opening Salvo
This particular phishing attack opened in much the same way as similar such attacks had over a year ago when we first reported on them. Last year the bad guys were leading with a very simple, short email that spoofed a senior executive in the organization being targeted.
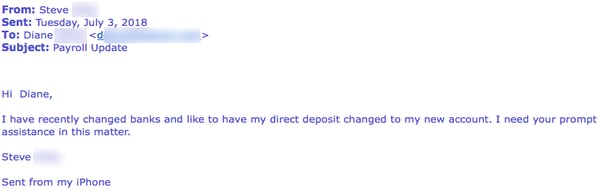
On the evidence of the phish reported to us just a few days ago, not much has changed.
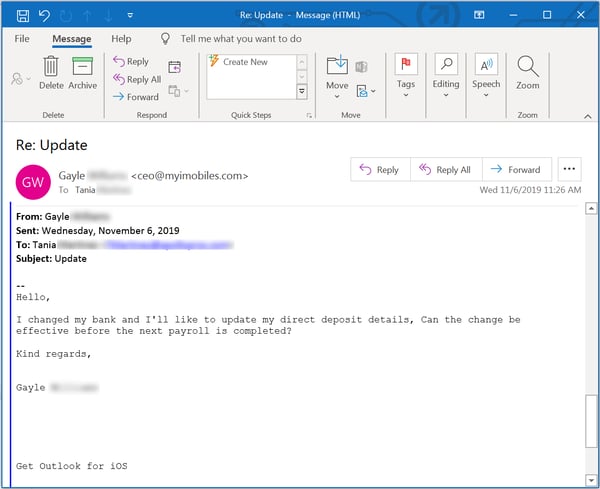
This more recent phish is a bit friendlier and not nearly as overbearing, but the essential thrust of the email is pretty much the same. From there, however, the two emails begin to diverge.
In last year's direct deposit phishes the bad guys began stumbling once employees began responding. These malicious actors were often stymied by the online payroll services they were frequently directed to. They were equally flummoxed by the required payroll change forms presented to them. And they were usually not equipped to provide copies of the cancelled checks requested of them.
As we noted:
These would-be fraud artists either don't have the required login credentials for the online payroll service (if they had the credentials, they already would have made the changes themselves, thank you) or they lack a cancelled check for the account they wish to start receiving direct deposits. Their usual response is to plead some form of inability to access the payroll service (a not particularly convincing excuse) or to claim that their checkbooks have mysteriously taken a walk. Both responses usually raise enough suspicion that someone hits the Phish Alert Button (PAB) and alerts IT staff.
In one case we documented the bad guys did manage to come up with photo of a cancelled check.

Even that amateurish effort fell flat, though, as...
this obviously photoshopped picture of a blank check [exhibits] a number of problems. First, the name on the check is visibly misaligned and lacking the usual address and phone information that most personal checks would sport. Second, the check number is 100 -- a clear indication that the bank account in question is brand spanking new. That was enough in this case for [the employee] to hit the Phish Alert Button (PAB).
Vive la différence!
Oh, how times have changed. In the email exchange reported to us just a few days ago, the bad guys were quick to seize the initiative once the employee responded.
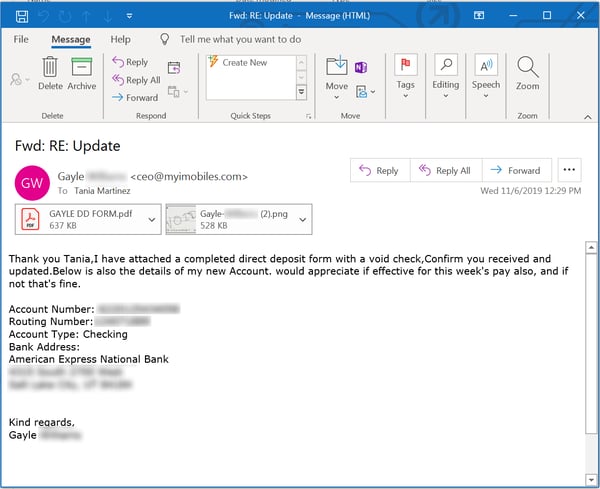
Take a good hard look. These people have done their homework. They are knowledgeable about the direct deposit process used at this company, completely prepared with all the required documents, and all too happy to cooperate. Indeed, the two attachments here speak volumes about how far the bad guys have come since last year.
First up is a copy of the company's "Direct Deposit Form" -- filled out by hand no less! (And just where did they get that document anyway?)
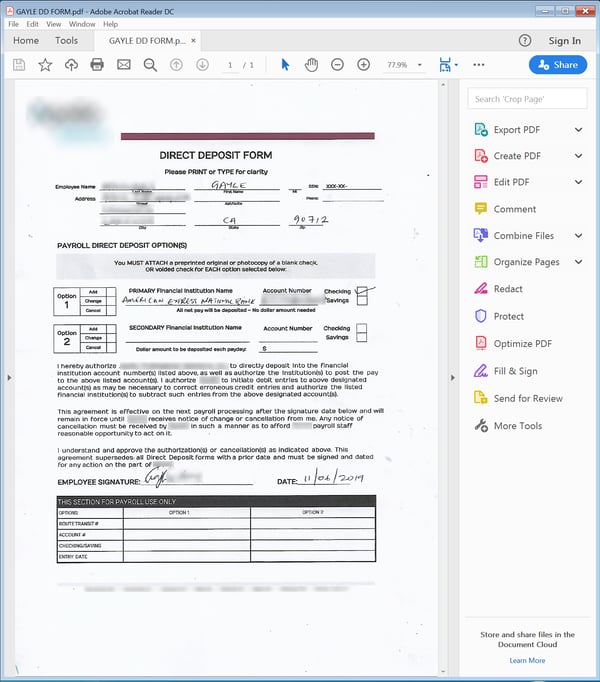
Next is a rather convincing picture of a cancelled check.

Compare the above with the cartoonishly bad check photo from last year.
If nothing else these email exchange speaks to the care and preparation the bad guys put in before springing this direct deposit phish on the targeted employee. They learned the process used at the company to make direct deposit changes, obtained the required form, and produced a nearly flawless copy of a voided check -- complete with a faux, hand-written "VOID" notice on the check itself. They also identified precisely the right employee to contact -- the company's payroll administrator.
What they hadn't counted on was encountering an employee who had been through New-school Security Awareness Training.
We don't know what ultimately tipped off Tania, the payroll administrator at this organization. Perhaps it was the transparently bogus email address used by the attackers. It might also have been the lack of a Social Security Number (which most folks would know off the top of their heads). Then again, it could have been the handwriting and signature on the direct deposit form. (In this case the bad guys were spoofing the founder and CEO of the company, whose unique hand would presumably be familiar to someone in Tania's position.)
Whatever it was, Tania took a good look and hit the Phish Alert Button (PAB), effectively pulling the plug on the bad guys' efforts to gin up a free payday for themselves.
Adapt or Get Fleeced
As we warned over a year ago, there's a very clear lesson for employees to learn here. You can't expect all the bad guys to be completely inept all of the time. Life just isn't that easy, much to our chagrin. Yes, they do make mistakes. But they learn fast from those mistakes. They adapt. And then they come back to take another run at your organization's money and resources.
If your employees aren't learning and adapting as well, there may well come a day when some very senior muckety-mucks in your organization suddenly discover they aren't receiving paychecks any more. Or your less senior employees may wake up to find their identities have been hijacked and their tax refunds stolen. Then everyone lawyers up and life becomes very unpleasant for all involved.
And here's the thing: no anti-virus application is going to stop that from happening. There is no malware to be found here. Only users who have been stepped through the latest New-school Security Awareness Training will ensure that everyone's money stays where it's supposed to.
 Here's how it works:
Here's how it works:




