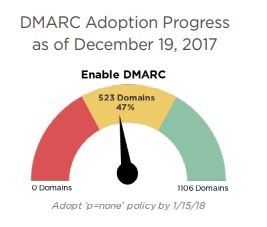
Nearly half of federal agency email domains have adopted policies to collect data on unauthorized emails, a move mandated by the Department of Homeland Security in October, according to a report by cybersecurity company Agari.
The new policies do not block malicious emails or prevent employees from receiving phishing emails, but instead allow email domain owners, such as CIOs, to receive reports on unauthorized messages sent through their domain.
The DHS mandate requires that all federal agencies adopt the Domain-based Message Authentication, Reporting and Conformance or DMARC monitoring policy at a level of “p=none” by Jan. 15. According to the DMARC.org frequently asked questions, a policy of “p=none” means that email domain owners receive reports on messages sent through their domain, but recipients still see the potentially malicious emails.
According to the Agari report, 151 domains established a DMARC policy for the first time between Nov. 18 and Dec. 18. This brings the total of agency domains meeting the DHS requirement to 47 percent.
The remaining 53 percent of domains, however, have less than two weeks to fulfill that requirement by the deadline. And even if adoption continues at the rate found by Agari, hundreds of federal domains will fail to meet the Jan. 2018 deadline.
“The analysis in this paper has shown that while federal agencies are making progress in the wake of the specific timelines set forth in [the DHS directive], most remain unprotected against phishing,” the Agari report said. “Almost 53% of federal agencies’ domains currently do not have a DMARC policy. For those that do, the majority still maintain a monitor-only ‘p=none’ policy that doesn’t protect their constituents. These agencies and their email recipients remain vulnerable to domain spoofing and phishing attacks.”
The (p=none) policy does nothing to block malicious emails, however, and agencies must implement a stricter policy to prevent employees from receiving phishing emails.
The DHS directives requires all agency domains to eventually move to a “p=reject” policy within a year of the mandate’s publication, which automatically rejects email messages that fail authentication. According to the Agari report, 15 percent of agency domains have already implemented this policy.
More at https://www.fifthdomain.com/cyber/2018/01/03/report-most-agencies-vulnerable-to-phishing/
Can hackers spoof an email address of your own domain?
Are you aware that one of the first things hackers try is to see if they can spoof the email address of your CEO? If they are able to commit "CEO fraud", penetrating your network is like taking candy from a baby.
Would you like to know if hackers can spoof your domain? KnowBe4 can help you find out if this is the case with our complimentary Domain Spoof Test. It's quick, easy and often a shocking discovery. Find out now if your email server is configured correctly, 82% are not!

Don't like to click redirected buttons? Get Started Here:
https://info.knowbe4.com/domain-spoof-test-chn




