 Threat actors are taking advantage of every free tool and service they can to improve their changes of successfully fooling security solutions, with compromised websites taking the lead.
Threat actors are taking advantage of every free tool and service they can to improve their changes of successfully fooling security solutions, with compromised websites taking the lead.
New data from Agari and PhishLabs in their just-released Quarterly Threat Trends & Intelligence report shows that those behind phishing attacks are relying on web services, tools, and hosting that would not be initially interpreted as being malicious in four out of 5 attacks. This has huge implications on security software designed to “follow” links within emails to establish that they aren’t malicious in nature.
According to the report, just under 83% of all technology, tools, etc. used by phishing attacks uses legitimate sites and services – of which nearly 42% represents compromised websites.
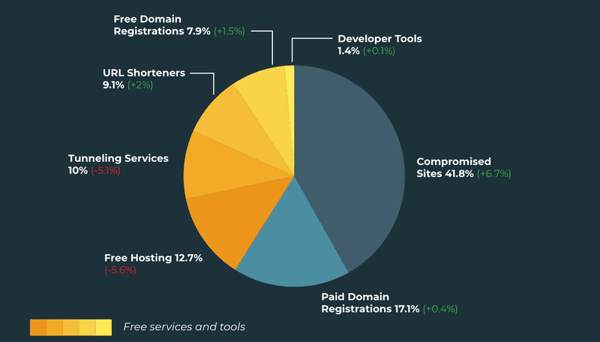
Source: Agari and PhishLabs
Also notable in the image able is the growth in the usage of compromised sites, free domain registrations, and URL shorteners – all indicators of tactics we will continue to see used to avoid detection.
These specific tactics also mean an increase in the use of social engineering, something only defeated by continual Security Awareness Training designed to educate users on what to look for when interacting with email. It’s evident that a portion of phishing emails will get through to the Inbox by using the above tactics; so be sure your users play a role in spotting and stopping phishing attacks by teaching them what a phishing attack looks like.
 Here's how it works:
Here's how it works:




