A phishing campaign is using a phony Google reCAPTCHA system to deliver banking malware, according to researchers at Sucuri. The attackers are sending emails, supposedly from a Polish bank, telling users to confirm an unknown transaction.
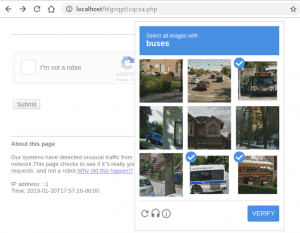
When recipients click on a link to investigate the suspicious charge, they’ll be shown a spoofed 404 error page. PHP code will then replicate a reCAPTCHA using HTML and JavaScript to trick victims into thinking the site is real.
The PHP code will then download either a .zip dropper or an .apk file, depending on which device the victim is using. If the victim is using Android, it will download malware that’s capable of intercepting incoming SMS, enabling the attacker to bypass SMS-based two-factor authentication.
The reason for the alternative serving of either a 404 or a reCAPTCHA page is to determine whether the target is suitable for infection. The 404 page appears if the malware detects a defined agent code. The bogus reCAPTCHA appears if the victim’s system passes through that test.
Luke Leal from Sucuri says there were some ways to identify the reCAPTCHA as fraudulent. “This page does a decent job at replicating the look of Google’s reCAPTCHA, but since it relies on static elements, the images will always be the same unless the malicious PHP file’s coding is changed,” says Leal. “It also doesn’t support audio replay, unlike the real version.” On the surface, however, the replica is very convincing.
Employees need to know that attackers are capable of tricks like this. Attacks can be complex, they can be targeted, and when they involve social engineering, they use small details like the familiar look of a reCAPTCHA page to throw the victim off guard. Phishing attacks are increasingly using new methods and technologies to confuse victims. New-school security awareness training helps your users keep up with these constantly evolving tactics.
Threatpost has the story: https://threatpost.com/phishing-scam-malware-google-recaptcha/142142/
Free Phishing Security Test
Find out what percentage of your employees are Phish-prone™
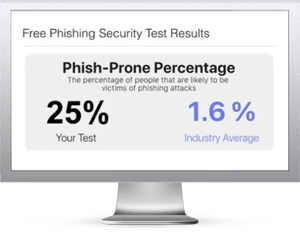
Would your users fall for CEO Fraud and other social engineering attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
 Here's how it works:
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://www.knowbe4.com/phishing-security-test-offer





