By Eric Howes, KnowBe4 Principal Lab Researcher. If you've been following the news over the past week or so then you know that a robust debate has opened at federal, state, and local levels in the United States over when and how to "re-open" the U.S. economy. Indeed, some European nations are already cautiously lifting some of the social restrictions imposed to control and suppress the spread of COVID-19.
Similarly, if you've been following the growth and development of Coronavirus-themed phishing emails over the past few months, you should also not be terribly surprised to learn that malicious actors have their own plan for re-opening businesses across the country.
Not only do they have a plan, they're starting to share it with your employees, most of whom will be keenly interested to know when they can resume something approaching a normal life after weeks of lockdown and finally return to the office.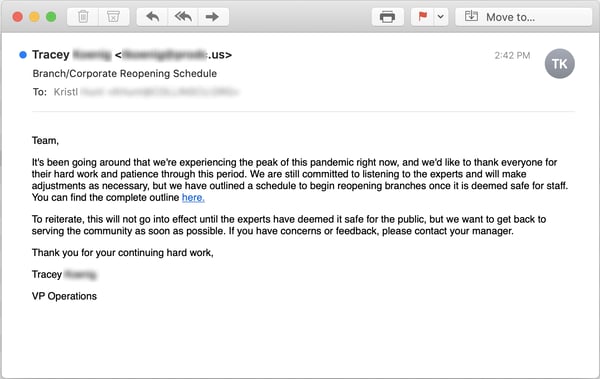
As phishing emails go, the prose here is absolutely pitch-perfect -- something even the most talented of malicious groups often struggle with when crafting social engineering schemes such as this one. The tone and language are familiar and hopeful, yet appropriately cautious and measured.
Nowhere will you find the hyperbolic excesses of so many of the virus-themed emails we've seen over the past few months. There are a few red flags here, to be sure -- the link, for starters, to say nothing of the From: email address. But your users need to be trained to look for them.
The payload is that familiar go-to for bad actors pushing dodgy HR announcements: Ye Olde Credentials Phish. 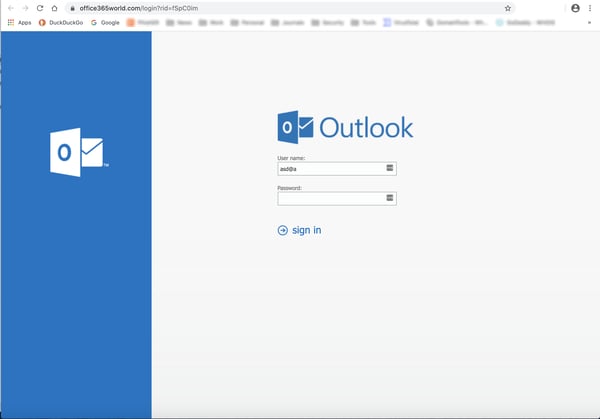
Coronavirus-themed social engineering schemes have become a natural part of the threat landscape at this point. Although we are past the initial hair-raising surge of malicious emails that defined the month of March, they remain a threat because the bad guys are proving themselves all too capable of exploiting the very latest news about the ongoing pandemic to dangle phish-bait in front of your users.
While your users may be safer at home in many respects -- social distancing does appear to be "bending the curve" -- they remain as vulnerable as ever to threat actors looking to leverage yours users' fears and concerns to get inside your organization's network.
Now more than ever your users need new-school Security Awareness Training to handle the very latest social engineering schemes such as this one.
Cancel
 New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!
