 New data shows a resurgence in successful ransomware attacks with organizations in specific industries, countries and revenue bands being the target.
New data shows a resurgence in successful ransomware attacks with organizations in specific industries, countries and revenue bands being the target.
While every organization should always operate under the premise that they may be a ransomware target on any given day, it’s always good to see industry trends to paint a picture of where cybercriminals are currently focusing their efforts. This gives organizations the ability to either shore up security measures today (if they’re a current target) or shore up security measures today anyways (so they’re ready for when they do become the target).
In third-party risk vendor Black Kite’s 2023 Ransomware Threat Landscape Report, we see some interesting trends around successful ransomware attacks today:
- March of this year saw 410 ransomware victim organizations – nearly double that of April of last year, with only 208
- The U.S. dominated as the primary focus, with 1171 victim organizations representing 43% of the total victims reported, with the UK, Germany, France, Italy, and Spain combined making up around 20% of victim orgs
- The largest group of victim organizations by revenue resided in the $50-60m range, with the next two groupings in the $40-50 million and $60-70 million ranges, respectively
- Manufacturing topped the list of industries, with “Professional, Scientific, and Technical Services” coming in second, representing nearly 35% of all victim organizations
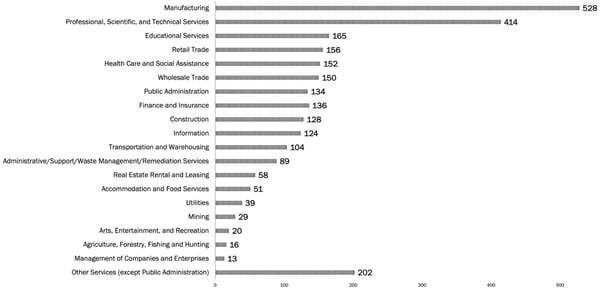
Source: Black Kite
In summary, it appears like cybercriminals are focused on mid-market, U.S.-based organizations that likely have a material amount of intellectual property and/or sensitive data.
This, of course, doesn’t mean if you’re not in that specific demographic you’re off the hook; nothing could be further from the truth. The Black Kite data shows where the focus is today. But there’s always a new player looking for a niche victim demographic they can nestle themselves into, making it necessary to shore up all security – including your user’s vigilance against phishing and social engineering attacks via Security Awareness Training.
 Here's how it works:
Here's how it works:




