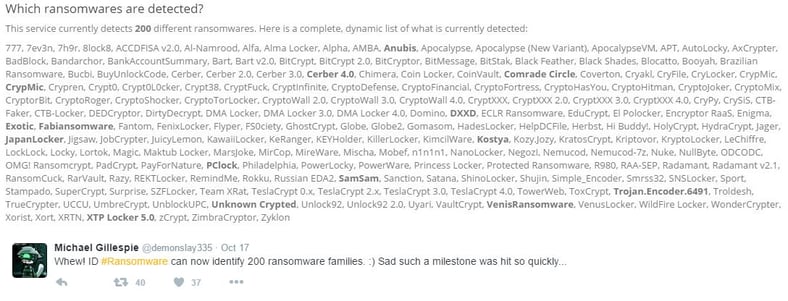
Michael Gillespie tweeted: "Whew! ID #Ransomware can now identify 200 ransomware families. :) Sad such a milestone was hit so quickly..." He added a list from the malwarehunterteam site, that gets added to dynamically. When you click this link, it will likely be more than 200.
Well, if you look at other malware statistics, this is still not even a drop in the bucket. There are millions of virus strains out there so just give it (a little bit of) time to reach the 1,000 ransomware strain count. Unfortunately this is going to be an exponential graph because more and more it will be fully automated, enterprise strength criminal malware creating more strains in an effort to evade detection.
Competing cybercrime mafias show the increasing commoditization of crypto-locking malware and the need for black hat developers to differentiate their wares in what is now an increasingly crowded marketplace. Kaspersky Labs estimates that between April 2015 and March 2016, there were more than 715,000 ransomware victims worldwide, or an increase of 5.5 times over the preceding 12-month period.
 BankInfoSecurity reported that efforts to block the bad guys are ramping up but are still in their infancy. The new European public-private No More Ransom project, launched July 2016, reports this week that at least 2,500 ransomware victims were able to download the portal's free decryptor tools - mainly for CoinVault, WildFire and Shade - and recover their data, avoiding paying more than $1 million in ransoms, happy project organizers say. However, that's just 0.35 percent of the total number of ransomware victims seen from April 2015 to March of this year.
BankInfoSecurity reported that efforts to block the bad guys are ramping up but are still in their infancy. The new European public-private No More Ransom project, launched July 2016, reports this week that at least 2,500 ransomware victims were able to download the portal's free decryptor tools - mainly for CoinVault, WildFire and Shade - and recover their data, avoiding paying more than $1 million in ransoms, happy project organizers say. However, that's just 0.35 percent of the total number of ransomware victims seen from April 2015 to March of this year.
No More Ransom launched as a joint venture between the Dutch National Police and Europol, as well as security firms Kaspersky Lab and Intel Security, a.k.a. McAfee.
Since then, law enforcement agencies from these 13 countries have also signed up: Bosnia and Herzegovina, Bulgaria, Colombia, France, Hungary, Ireland, Italy, Latvia, Lithuania, Portugal, Spain, Switzerland and the United Kingdom.
Would be nice to see a similar initiative in North America as well!
But for now, every organization is going to be exposed to this type of cyber harassment that is part of a simmering internet cold war between the US, Russia and China.

Your Last Line Of Defense: Employees
Ransomware is now so successful and profitable that it has drawn in the largest, well-funded malware mafias who continue to furiously innovate in an attempt to grab market share from each other.
For every under skilled, overly confident new entrant into the ransomware market there is at least one extremely clever group of malicious actors capable of building effectively uncrackable crypto-prisons for your company's data. And when your data goes to malware jail, your organization suffers downtime, data loss, possible intellectual property theft, and in certain industries like healthcare, ransomware infections are now looked at to possibly be a HIPAA violation resulting in heavy fines.
With every new ransomware strain it becomes increasingly important to shore up your company's last line of defense: your employees. That means ensuring that your users have been given effective security awareness training to identify social engineering red flags, whether they come through malvertising on exploit-laced web pages or deviously crafted phishing emails that make it through your filters.
 This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:




