 More than 4,000 ransomware attacks occur daily and healthcare is the largest target. However, despite disclosure requirements and the risk of late or no HIPAA notification at all, breach reporting simply doesn’t match up.
More than 4,000 ransomware attacks occur daily and healthcare is the largest target. However, despite disclosure requirements and the risk of late or no HIPAA notification at all, breach reporting simply doesn’t match up.
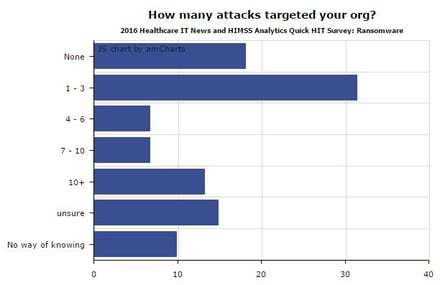
I found some interesting data in a new survey by Healthcare IT News and HIMSS Analytics that showed more than half of hospitals were hit with ransomware from April 2015 to April 2016, but breach reporting to the OCR was practically non-existent.
The Office for Civil Rights (OCR) is an organization within the U.S. Department of Health & Human Services (HHS). Under the Health Insurance Portability and Accountability Act (HIPAA), the OCR can levy significant fines to health care providers and their business associates if personal health information is lost or stolen.
As ransomware attacks have increased, one would expect OCR breach reporting to have increased more or less concurrently, but only nine (!) organizations reported malware or ransomware breaches to OCR in 2016.
"Because ransomware is so common, hospitals aren't reporting them all," said ICIT Senior Fellow James Scott. "And ransomware is just the start for more specific actors to send in another attack and start mapping the system."
Four Reasons Why Breaches Do Not Get Reported
There are four major reasons hospitals don't report breaches, said ICIT's Scott.
- To start, there's a fear of the economic impact and liability resulting from having to admit an organization has put thousands or millions of unsuspecting patients at risk for a lifetime of being exploited by criminals.
- Further, many employees, from executives to entry-level personnel don't want to admit to administration or to the IT team they fell for a social engineering scam. As a result, these employees don't report their mistake.
- Another major issue is that an investigation can disrupt business operations. Not only that, but investigators "poke holes in examined networks and publicize the vulnerable network that, in all likelihood, is already pulsating with scores of adversaries, who have been exfiltrating data all along," Scott said.
- "Negative publicity harms reputation and diminishes deniability, thereby making the victim organization more liable in future cyber-incidents," Scott explained. "Nowadays, if a health sector organization is only hit with ransomware, they can consider themselves lucky and perhaps those are the breaches that we hear about."
You have 60 Days To Report
The 60-day timer starts the moment a breach is discovered, which is the first day the covered entity knew about the breach. And it applies to all staff within the organization. For example, when someone at the help desk learns about a breach, the timer starts then – even if it takes a week for the incident to be reported to higher staff, according to Erin Whaley, a partner at Troutman Sanders in Richmond, Virginia.
"However, many healthcare organizations remain non-compliant out of calculated non-compliance (the fine is cheaper than the reporting costs and impact) or out of lack of resources (they cannot afford the technical controls, contractors and other needs to investigate incidents to HHS satisfaction," he added. "Considering that some hospitals are seeing 20 or more ransomware attacks per day, hesitance to report out of fear or reputation loss or lack of resources, is not surprising."
 This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:




