 Crysis decryption keys posted
Crysis decryption keys posted
The decryption keys of the Crysis ransomware were posted on Pastebin, which allows victims to decrypt their hijacked files without paying. Crysis was notorious for spreading through attacks on the Windows Remote Desktop Protocol, using brute force attacks.
Why the keys were released is also unknown, but it may be due to the increasing pressure by law enforcement on ransomware infections and the developers behind them. Kaspersky recently added the decryption keys to their ransom-decryption tool and the BleepingComputer site explained how to get your files back.
Ransomware hijacks UFCW Local 655 Food Employers Joint Pension Plan
Recently, all files on a server of UFCW were encrypted and they sent a message to their 18,000 members that their data had possibly been stolen, including their name, DOB, SSN and account number. The fund was managing around 500 million dollars, and discovered they had been hacked a week before the ransomware infection kicked in.
The attacker demanded 3 Bitcoins, around 2,000 dollars -- but UFCW decided not to pay and restore from backups, Bloomberg reports. It is unclear how the hackers got access and what ransomware strain it was.
New strain uses Social Media profile of victim
Researchers at Proofpoint dug up a new browser locker variant that uses Facebook, Skype and LinkedIn profile information and download history to extort money from victims. The strain is called Ransoc and spreads through malvertising -- infected malicious ads on legit websites.
Once the machine is infected, Ransoc searches for files that were downloaded through torrent sites and shows a warning which included the victim's social media data:
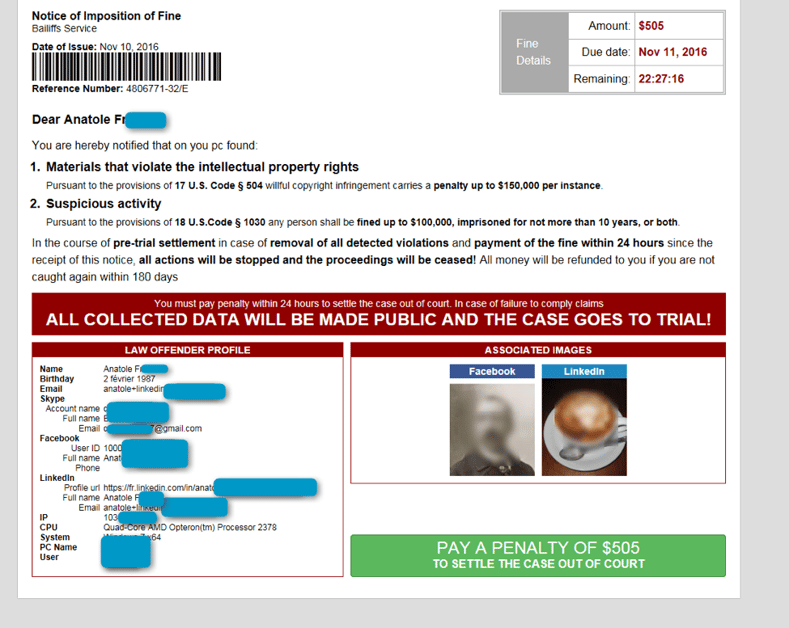
This is more "Blackmailware" than ransomware as these criminals go after the reputation of the person instead of their files. Moreover, they are pretty brazen because they allow the victim to pay with a credit card, which is relatively easy to trace back.
The malcode disables RedEdit, MSconfig and the Taskmanager but only adds a key to the Registry, so a restart in Safe Mode and taking out that key is sufficient to remove the infection.
Microsoft warns: fake fax attachments are really ransomware
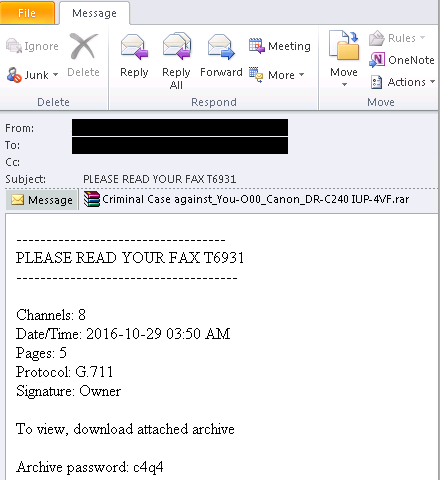
Microsoft warned against a spam campaign that tries to social engineer users to open the attachment which is a fake fax attachment which contains a "Criminal case against you”.
They discovered a new threat that uses email messages pretending to be fax messages, but in truth deliver a ransomware downloader. The attachment is a password-protected RAR archive file that, when extracted, is a trojan. The user is social engineered to put the password into the archived file to unzip it.
Ransomware criminals ask expert to help them debug their code
A well known malware researcher was asked to help debug some criminals code and he publshed the request in a tweetstorm explaining what was being asked. A bug in the code caused some of the hijacked files to be overwritten so that they were permanently lost. The bad guys needed help with their use of CryptoAPI and decided to ask Fabian Wosar. Here is what they said:
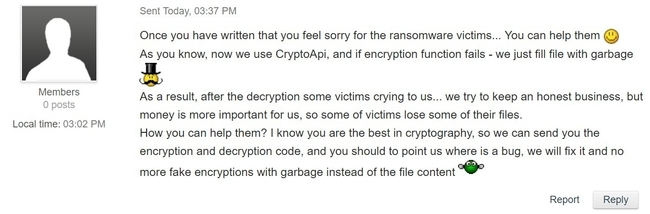
Fabian asks: "What would you do? Would you help them?"
Karma Ransomware being distributed via Pay-per-Install Network
Larry Abrams wrote: "A security researcher named slipstream/RoL has discovered the Karma Ransomware, which pretends to be a Windows optimization program called Windows-TuneUp. What is worse is that this sample was discovered as software that would potentially be distributed by a pay-per-install software monetization company when people install free software downloaded from the Internet. " Here is how it looks:
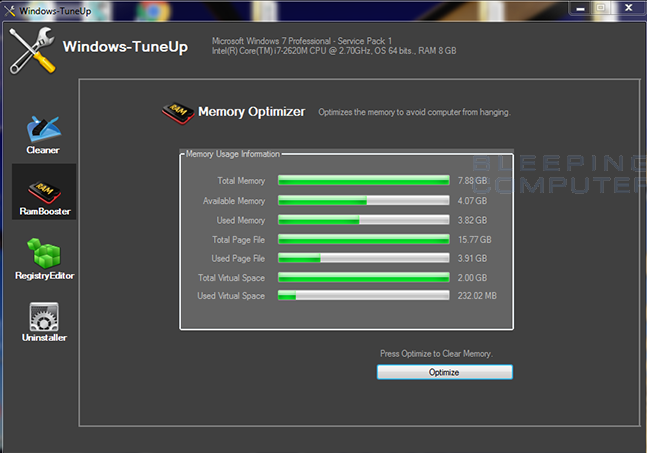
Bundled software is getting more dangerous by the month.
Seven Months Later, ID Ransomware Can Detect 238 Ransomware Families
Catalin Cimpanu wrote: "Ever since it launched in April 2016, the ID Ransomware service has been slowly, but surely, becoming the default destination for victims looking for information to aid them in solving their ransomware infections.
If you haven't heard of it by now, ID Ransomware, sometimes referred to just as IDR, allows ransomware victims to upload a copy of their ransom note along with an encrypted file to a specialized website.
After the portal's backend analyzes the submitted data, it will try to identify the ransomware that has locked the user's computer by looking at several clues such as the ransom note text, the Bitcoin address used, email addresses found in the ransom note, and more.
The service has been immensely useful, and according to Michael Gillespie, the man that has put it together, has received 158,577 submissions from 81,965 unique IPs."
Free Ransomware Simulator Tool
How vulnerable is your network against ransomware attacks?
Bad guys are constantly coming out with new versions of ransomware strains to evade detection. Is your network effective in blocking ransomware when employees fall for social engineering attacks?
KnowBe4’s Ransomware Simulator "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 ransomware infection scenarios and show you if a workstation is vulnerable to infection.
Don't like redirected buttons? Cut & Paste this link in your browser:
https://www.knowbe4.com/ransomware-simulator





