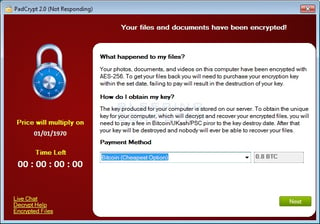
 To start with, a new ransomware strain with many similarities to CryptoWall called PadCrypt was discovered yesterday that for the first time includes a live support chat screen and an uninstaller for the infection itself. The uninstaller unfortunately does not decrypt the files though. As of now the C2 servers are down, so no files will actually be encrypted and the live chat functionality does not work.
To start with, a new ransomware strain with many similarities to CryptoWall called PadCrypt was discovered yesterday that for the first time includes a live support chat screen and an uninstaller for the infection itself. The uninstaller unfortunately does not decrypt the files though. As of now the C2 servers are down, so no files will actually be encrypted and the live chat functionality does not work. Skype Malvertising Spreads Ransomware
Cybercriminals have been able to use malvertising to penetrate Microsoft's Skype platform and show ads that infect their machine with malware using the Angler exploit kit, anti-virus company F-Secure reports. Angler uses vulnerabilities in unpatched installations of Adobe's Flash player to infect the machine with TeslaCrypt. The malvertising came via the AppNexus ad-platform which has been used in the past to spread malvertising.
DMA Locker Ransomware targets Unmapped Network Shares
DMA Locker is a new ransomware that was discovered last week by PhysicalDrive0 and analyzed by Malwarebytes malware analyst Hasherezade. This ransomware encrypts your data using AES encryption and then demands 4 bitcoins to receive your decryption key. Earlier versions were decryptable due to a flaw in the program, but newer versions have resolved this issue. DMA Locker includes some interesting features including the encryption of unmapped network shares and the targeting of any file that does not reside in a particular folder and or does not have particular extensions. More at Bleeping Computer.
Surgeries in Hospitals Postponed Because Of Ransomware Infection
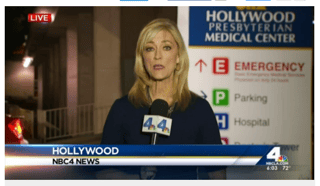 A Southern California hospital was a victim of a cyber-attack, interfering with day-to-day operations, the hospital's president and CEO said. Staff at Hollywood Presbyterian Medical Center began noticing "significant IT issues and declared an internal emergency" on Friday, said hospital President and CEO Allen Stefanek, NBC reported on TV, A doctor who did not want to be identified said the system was hacked and was being held for ransom. There is no information that any patient or employee information was compromised, but the hospital called in computer forensics experts, and the FBI and the LAPD to investigate.
A Southern California hospital was a victim of a cyber-attack, interfering with day-to-day operations, the hospital's president and CEO said. Staff at Hollywood Presbyterian Medical Center began noticing "significant IT issues and declared an internal emergency" on Friday, said hospital President and CEO Allen Stefanek, NBC reported on TV, A doctor who did not want to be identified said the system was hacked and was being held for ransom. There is no information that any patient or employee information was compromised, but the hospital called in computer forensics experts, and the FBI and the LAPD to investigate.
An email attachment caused an infection at a German hospital in Neuss, and patient records were encrypted and not accessible. According to the German RP Online, many more hospitals that area were infected with ransomware. Out of the six infected hospitals, only the one in Neuss announced the fact publicly, and called it an "IT problem". Medical staff needed to fall back on paper systems, and the hospital is not planning to pay the ransom fees as they are restoring their backups.
It is highly likely that these infections were caused by employees that were social engineered and did not get effective security awareness training. Get the most informative and complete ransomware hostage rescue manual. This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware.





