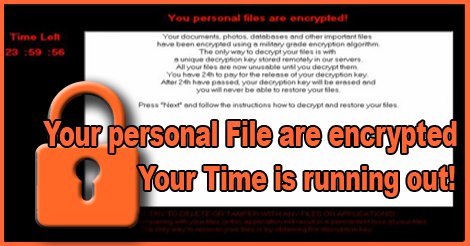
DecryptorMax 24-hour deadline
Ransomware strains use different ways to pressure victims into paying, varying from 7 days after which the ransom doubles, to threatening to publish files on the Internet if the ransom is not paid.
A brand new variant makes things even more frantic, because it uses a 24-hour deadline to pay or lose all the files. This new strain is the DecryptorMax-ransomware which like all other strains encrypts all the files when a system gets infected.
After all files are locked, a notice shown above appears on the screen that ransom is required to get the files back. DecryptorMax victims have just 24 hours to pay, and if they fail to pay, the decryption key will be deleted which means the files will be lost forever. According to Botfrei, a German collective of antivirus and telecom companies, this strain tries to intimidate victims with a very short deadline. Botfrei suggest that victims do not pay, as there is no evidence yet that paying victims actually get their files back. That leaves you with having to restore from backup, if you have that option.
Researchers Crack Linux.Encoder
Researchers have been able to crack the Linux.Encoder-ransomware, so victims can get their files back without having to pay. This new strain was announced last week by the AV company Doctor Web. At that time it was not known yet how the ransomware infected systems, however it was clear that predominantly webservers were targeted. Antivirus company Bitdefender however, announced that there is a vulnerability in the Magento content management system, that allows hackers access to servers. Later it was found that unpatched WordPress servers were also infected.
Next, they install the ransomware which encrypts Linux.Encoder files with AES. This symmetric key then gets in turn encrypted with an asymmetric encryption algorithm (RSA) and a 1 Bitcoin ransom is demanded: "We are accept only Bitcoins". The developers of Linux.Encoder made an error in the design of their malicious code, so that Bitdefender researchers could recover the AES-key without using the private RSA key. You can download a tool (zip) that helps you to automatically decrypt the files, until the bad guys correct their error and come out with a new version. A researcher from F-Secure estimated that the cyber criminals made about 12,000 Euro in one month.
Ransomware Infects British Parliament Computers
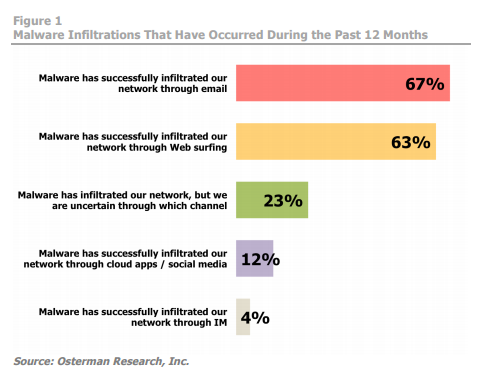 A recent report from Osterman Research showed that email still is the number one infection vector (with web surfing a close second), which points to end-users being social engineered and clicking on malicious links and opening infected attachments.
A recent report from Osterman Research showed that email still is the number one infection vector (with web surfing a close second), which points to end-users being social engineered and clicking on malicious links and opening infected attachments.




