 With the much-anticipated annual Verizon Data Breach Investigations Report finally released, we get a view of ransomware from the data breach perspective that points to a common weakness in your security strategy.
With the much-anticipated annual Verizon Data Breach Investigations Report finally released, we get a view of ransomware from the data breach perspective that points to a common weakness in your security strategy.
When it comes to the state of your organization’s ability to protect itself against cyberattacks – and ransomware, specifically – I truly don’t want to be the one that says “I told you so.” But the new data in Verizon’s Data Breach Investigations Report paints a pretty conclusive picture around why ransomware attacks are so successful.
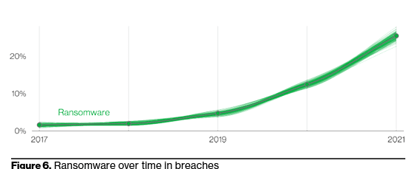
First off, I need to point out that while 25% of data breaches involve ransomware, that number is nearly double what Verizon found in 2020 – demonstrating that, from the data breach perspective, we’re seeing ransomware attacks begin to encroach themselves as a dominant factor in data breaches (and will likely continue to do so).
So, what’s helping ransomware-involved data breaches be so successful? In a word… users.
According to Verizon, 82% of data breaches (ransomware included) involve “the human element” (which Verizon cites as including “Use of stolen credentials, Phishing, Misuse, or simply an Error”). Take a look at the chart below from the report, showing the action varieties found within ransomware-involved incidents:
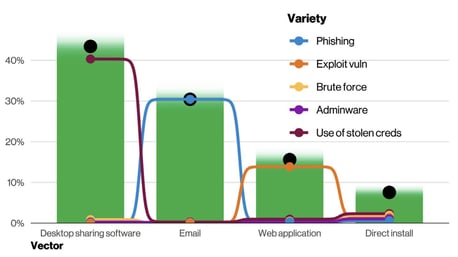
What you should notice is that three of the four (desktop sharing software, direct install, and email) all imply access to either a user’s endpoint or their web-based email. And how does one get such access? Usually through phishing attacks intent on either compromising credentials (in the case of email) or the user’s endpoint (in the case of desktop sharing software and direct install).
Verizon calls credentials and phishing two of “the four key paths leading to your estate” (in addition to exploiting vulnerabilities and botnets). They go on to state “These four pervade all areas of the DBIR, and no organization is safe without a plan to handle them all.”
Let’s sum this one up, shall we?
Ransomware is on the rise, users are involved somehow in a majority of all data breaches, threat actors gain access to endpoints and email, and phishing pervades all of this. Seems to me that the issue here (when you rewind the clock back to the initial threat actions that allow these ransomware incidents to occur) is users falling prey to phishing attacks – something easily either reduced or remedied with Security Awareness Training.
There’s no more respected or trusted report out there than the Verizon DBIR. So if Verizon is telling you users are the key to successful ransomware attacks, and that phishing is one of the keys to your kingdom, you need to be doing something about it to mitigate the user risk that exist within your organization.
 Here's how it works:
Here's how it works:




