 As attackers evolve their toolsets and processes, the significant drop in dwell time signifies a much higher risk to organizations that now have less time to detect and respond to initial attacks.
As attackers evolve their toolsets and processes, the significant drop in dwell time signifies a much higher risk to organizations that now have less time to detect and respond to initial attacks.
This is bad news.
Two years ago, the median dwell time – the time between gaining access to a network and executing the ransomware – was 5.5 days. Last year it was 4.5 days. This year, it’s slightly less than just 1 day, according to Secureworks’ 2023 State of the Threat: A Year in Review report covering the 12-month period from July of 2022 through June of 2023.
The massive reduction in dwell time means two things. First, threat actors are able to perform discovery and lateral movement faster than ever before. Second, you have a single day to detect an attack that is designed to not be identified.
In other words, the cybercriminals are winning. It’s likely this quickening of dwell time is resulting in more successful attacks, as demonstrated by the continual increase in the number of “name and shame” victim organizations, as shown below.
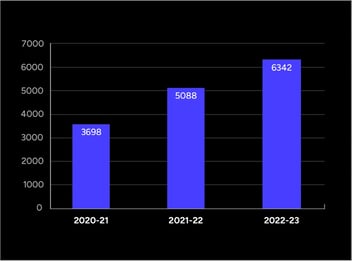
Source: Secureworks
This data makes it clear that organizations need to improve their detection and response capabilities, as well as to increase their ability to avoid successful ransomware attacks altogether by minimizing the effectiveness of the primary initial attack vector – phishing. This is accomplished through continual employee security awareness training that educates the user on how to remain vigilant and minimizing the risk of a successful attack.
KnowBe4 enables your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
 This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
This 26-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:




