The criminal gangs that live off ransomware infections are targeting Small Medium Business (SMB) instead of consumers, a new Trend Micro Analysis shows. The reason SMB is being targeted is that they generally do not have the same defenses in place of large enterprise, but are able to afford a 500 to 700 dollar payment to get access to their files back.
The other reason that ransomware attacks on SMB's are often successful is that their backup solutions are often not very sophisticated or not being done at all. The new figures from Trend Micro show that it's very often SMB employees that click on emails with malicious attachments, and they are usually received in the early morning hours.
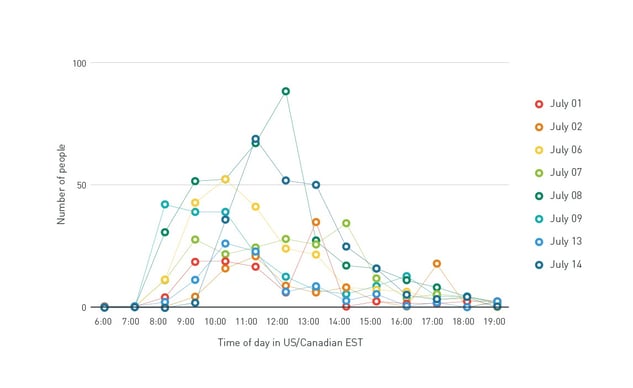
Trend Micro analyzed June-July 2015 time frame with clicks on links of CryptoWall ransomware. A whopping 67% of the links were opened by SMB's. large enterprise followed with 17%, and third came consumers with just 13%. The remaining 3% fell in the "Other" category.
Time Zone
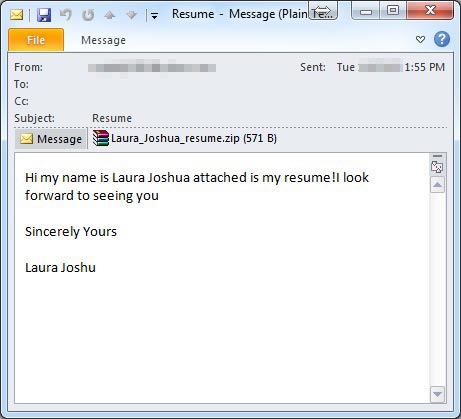
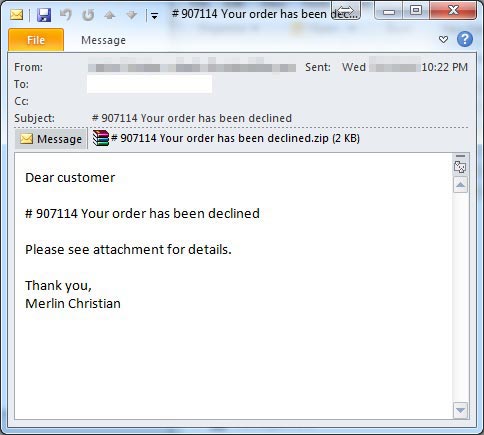
Sending the phishing emails is closely timed with early morning business hours of the victims. Most of the messages are sent at the start of the working day, an indicator that cyber crime is moving towards business victims. Most of the infections turn out to be caused between 9am and 1pm. And obviously the emails themselves focus on employees resumes and invoices are usually used as phishing bait. Here are some examples:
Trend Micro said: "TorrentLocker and CryptoWall pose serious risks to a company’s confidential data. However, SMBs can protect their network via vigilance and awareness of such security risks. Simply verifying emails first and checking the reputation of websites before visiting can go a long way. It’s also recommended that employees do not enable macros by default to avoid the execution of CryptoWall. We cannot stress enough the importance of backing up files, following the 3-2-1 rule as best practice. Empowering employees with awareness and knowledge on security threats and their social engineering lures is one step in defending your network. SMBs should have a security solution that protects their system and network from all layers against threats like ransomware via detecting malicious file and spam, and blocking related URLs."
Now would be a good time to refresh your users on the 22 social engineering red flags to watch out for, we suggest you print out the PDF and pass it along to coworkers as well as family and friends:

Effective security awareness training that combines interactive training and frequent simulated phishing attacks is a must these days. Find out how affordable this is today and be pleasantly surprised.