.jpg?width=400&name=iStock-1284465103%20(1).jpg) The ransomware attack occurring in late-May required the maker of consumer and industrial memory products to take systems offline, causing them to recover and upgrade affected systems.
The ransomware attack occurring in late-May required the maker of consumer and industrial memory products to take systems offline, causing them to recover and upgrade affected systems.
Ragnar Locker hasn’t been in the news much since they became a part of the Maze extortion cartel in the middle of last year. But their latest attack on ADATA signals they aren’t going anywhere and are succeeding in infiltrating and encrypting victim environments.
In an email statement to Bleeping Computer, ADATA confirmed the attack on May 23rd which disrupted business operations. And while no details were released, it appears from the email communications, ADATA was successful in implementing a response plan:
“The company successfully suspended the affected systems as soon as the attack was detected, and all following necessary efforts have been made to recover and upgrade the related IT security systems.”
The bad guys at Ragnar have claimed responsibility for the attack, alleging they have stolen 1.5TB of data – which can include intellectual property, source code, legal documents, confidential files, and more.
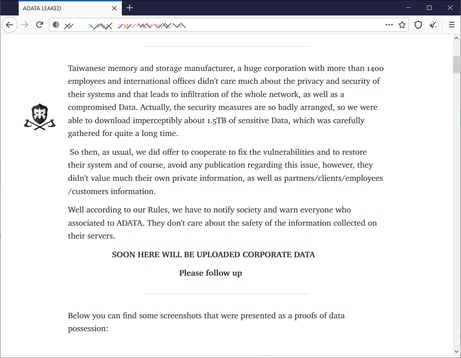
Source: Bleeping Computer
The upside to this story is ADATA signifies that it’s possible to have proper response plans in place when you’re hit with ransomware to minimize operational disruptions. The downside is ADATA – and any other organization in their same situation – now has to content with what to do about the stolen data. Remember, ransomware gangs aren’t just arbitrarily taking whatever data they find; they are inspecting all the data they have access to and selectively choosing what data to exfiltrate.
Ragnar has historically gained access via phishing attacks, which are largely preventable with Security Awareness Training that enables users to elevate their attentiveness when interacting with suspicious email and web content.
 Here's how it works:
Here's how it works:




