We've been reporting on the top-clicked phishing email subjects every quarter for a while now across three different categories: general emails, those related to social media, and 'in the wild' attacks that are a result of millions of users clicking on the Phish Alert Button on real phishing emails and allowing our team to analyze the results.
Make Your Users Think Twice
Sharing the latest threats with users is a great way to keep them on their toes. Also we see a lot of similarities in the subjects quarter over quarter, so knowing what the popular ones are can help them to stay vigilant and ultimately think twice before clicking. The bad guys continue to take advantage of the human psyche and bypass rational behavior.
Using Human Nature Against Us
“Hackers are smart and know how to leverage multiple psychological triggers to get the attention of an innocent victim. In today’s world, it’s imperative that businesses continually educate their employees about the tactics that hackers are using so they can be savvy and not take an email at face-value. Hackers will continue to become more sophisticated with the tactics they use and advance their utilization of social engineering in order to get what they want,” said Perry Carpenter, chief evangelist and strategy officer at KnowBe4.
Here is a visual representation of top messages for the last quarter:
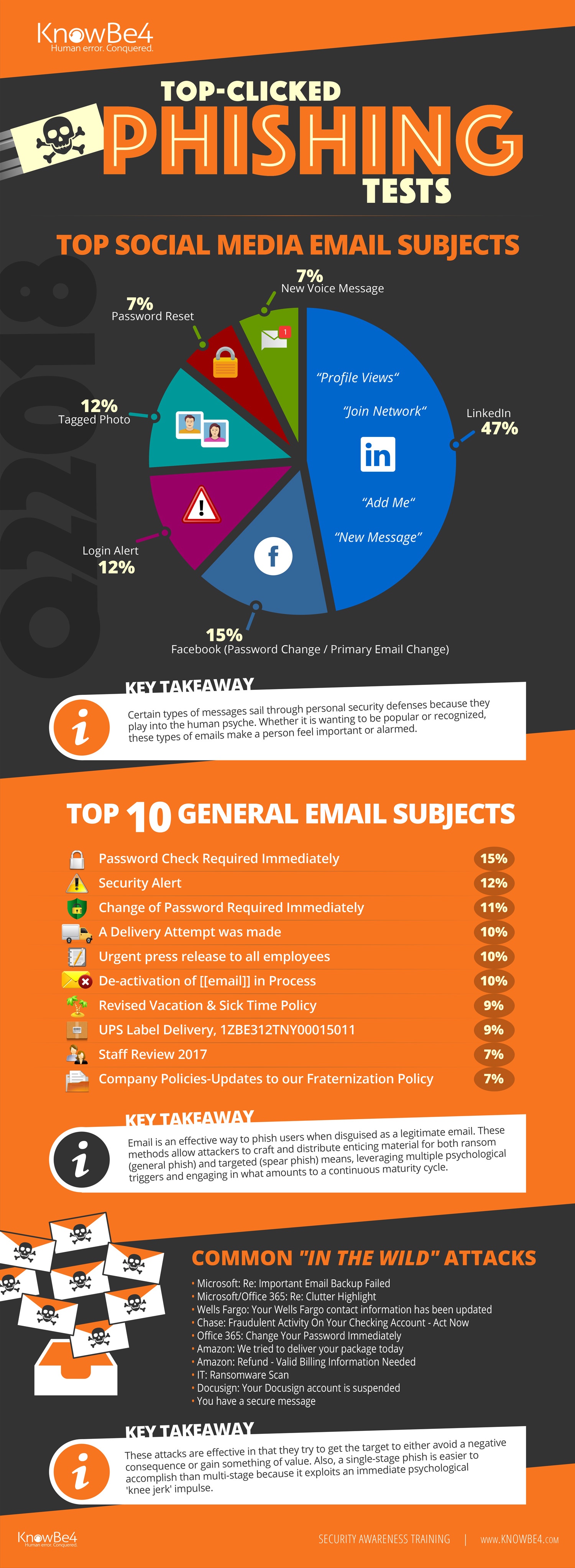
The Top 10 Most-Clicked General Email Subject Lines Globally for Q2 2018 include:
- Password Check Required Immediately 15%
- Security Alert 12%
- Change of Password Required Immediately 11%
- A Delivery Attempt was made 10%
- Urgent press release to all employees 10%
- De-activation of [[email]] in Process 10%
- Revised Vacation & Sick Time Policy 9%
- UPS Label Delivery, 1ZBE312TNY00015011 9%
- Staff Review 2017 7%
- Company Policies-Updates to our Fraternization Policy 7%
*Capitalization and spelling are as they were in the phishing test subject line
**Email subject lines are a combination of both simulated phishing templates created by KnowBe4 for clients, and custom tests designed by KnowBe4 customers
Most common ‘in-the-wild’ emails in Q2 2018 included:
- Microsoft: Re: Important Email Backup Failed
- Microsoft/Office 365: Re: Clutter Highlight
- Wells Fargo: Your Wells Fargo contact information has been updated
- Chase: Fraudulent Activity On Your Checking Account – Act Now
- Office 365: Change Your Password Immediately
- Amazon: We tried to deliver your package today
- Amazon: Refund - Valid Billing Information Needed
- IT: Ransomware Scan • Docusign: Your Docusign account is suspended
- You have a secure message
*Capitalization and spelling are as they were in the phishing test subject line **In-the-wild email subject lines represent actual emails users received and reported to their IT departments as suspicious. They are not simulated phishing test emails.
Organizations worldwide stand to lose an estimated $9 billion in 2018
A new report from NIST says one of the most important factors around whether a user clicks a phishing email or not is context. If the subject is highly relevant to the recipient, they are more likely to click. Phishing is all about convincing the recipient that the email is valid and, therefore, needs to be read and addressed. As humans, we look at the email and derive its context to determine whether we believe it’s necessary to open, read, and click through.
So how do you get users to stop clicking on phishing emails with high relevancy?
According to NIST, there are three parts to the strategy:
- More User Education – Users need to be trained on the latest scams, methods, and be taught what to look for. This is better known as Security Awareness Training.
- More Technology – NIST feels the solutions put in place need to move beyond just being reactive, and focus on stopping a threat before it ever even has a chance. This is where layers of defense in depth come into play.
- User Reporting – Organizations need to make it easier for users to report attacks to IT. This allows IT to respond, including informing the remainder of the user base, minimizes the threat potential and the damage. Here is a way to do that for free.
 Here's how it works:
Here's how it works:




