Slack, the ubiquitous communication and collaboration platform, has been getting more and more attention over the past few months as a potential phishing platform and target for malicious actors. Most of this attention has settled on various methods to phish users within Slack itself, and the concerns range from DMs to Slackbot reminders and public Slack channels or workspaces.
Much of that ongoing discussion is focused on the use of publicly leaked Webhooks to inject malicious messages into Slack channels. And, unsurprisingly, we already have reports of this method being used in Slack workspaces, esp. those with with public channels devoted to crypto-currency-related topics and discussions.
Slack can be used for phishing users outside of Slack, though. One reported scheme, for example, involves using Slack's "referral URL" domain, slack-redir.net, to launder malicious links, allowing them to sail past multiple layers of security given that Slack domains will generally be trusted.
Indeed, we began receiving reports from customers using the Phish Alert Button (PAB) of malicious emails using this method back in late November of 2019.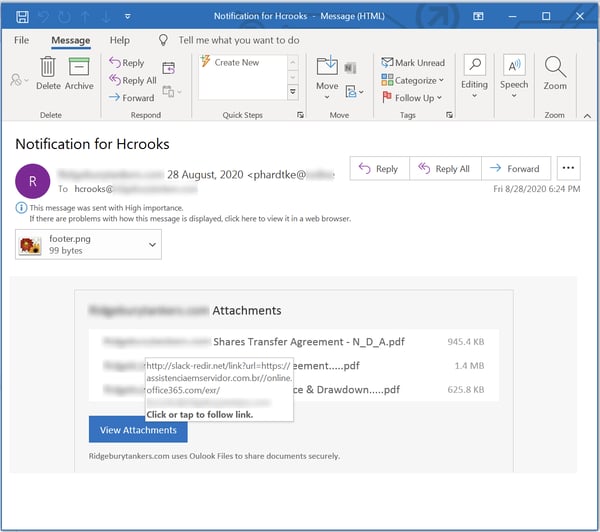
Emails exploiting the domain slack-redir.net have tended to land users at credentials phishing landing pages hosted on third-party web sites.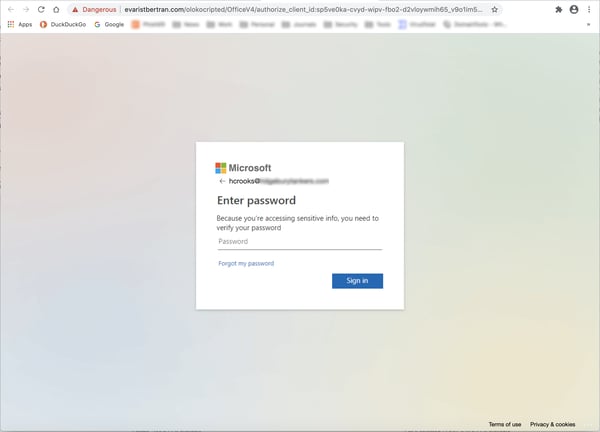
In late June of this year, however, customers starting reporting malicious emails using Slack in quite another way: as a host for malicious files used as part of phishing attacks.
Let's take a look at how this works.
The Attack
The attack method involved is a fairly familiar one in which the bad guys find a legitimate site or service that can be abused to host malicious files that can then be deployed to facilitate email-based phishing attacks.
The bad guys clearly, and for obvious reasons, prefer sites and services that can be used for free (whether legitimately or not). To that end, they prefer sites and services that allow unknown users to create free accounts, though they are perfectly happy to use compromised pay accounts at online services if such accounts offer key benefits like, say, the ability to blast large volumes of malicious emails out to potential victims. And if the domain being used is recognized and trusted by your average cubicle dweller within businesses and organizations across the country or around the world, so much the better.
In this case, the target is Slack's file storage domain, slack-files.com, which is typically used to host files uploaded by users within Slack itself. Indeed, Slack freely advertises Slack's robust file management and collaboration features, which include integration with third-party apps.
Here's a typical malicious email we've seen using slack-files.com to execute what amounts to a three-stage phishing attack.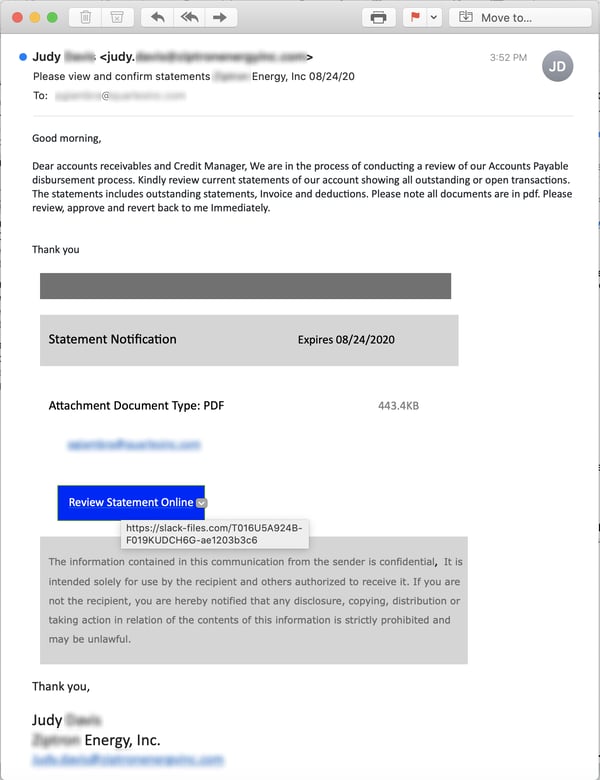
Most of the emails we've seen using slack-files.com are formatted in a similar fashion, suggesting this scheme is being used by only a small number of malicious groups at present.
The link in the email takes users to a PDF file hosted on slack-files.com...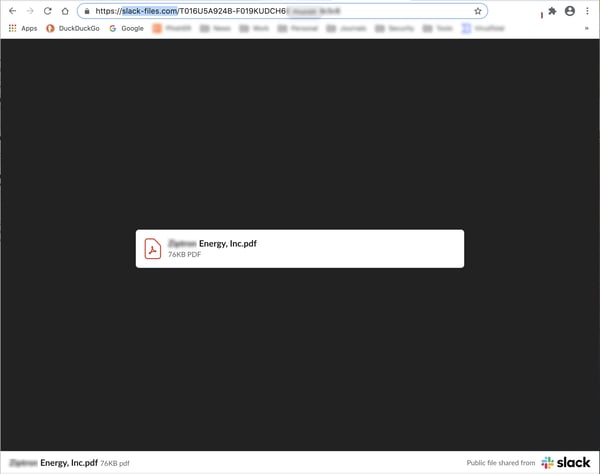
...which users must download and open: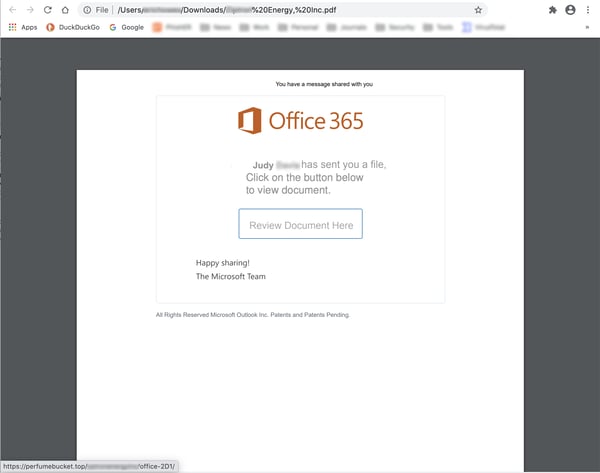
The link in that email shuffles users on to yet another site, which is usually hosting a credentials phish of one sort or another: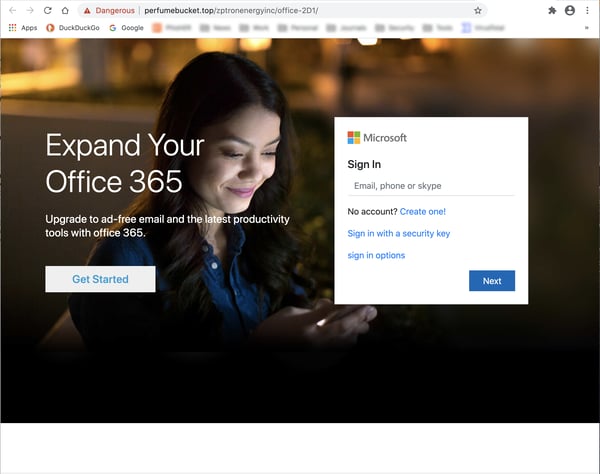
Occasionally we see emails exploiting slack-files.com use a strikingly different format: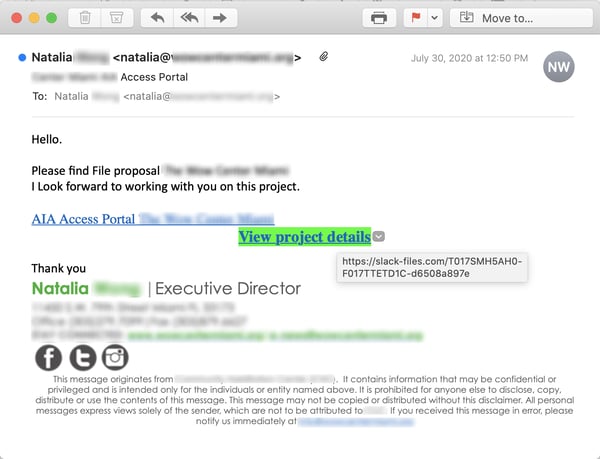
The second and third stages of the attack tend to follow the same pattern as the first email documented above, though.
This three-stage attack using files hosed at a legitimate online service or site is hardly new or unique. It is, in fact, the same pattern we've seen used to exploit and abuse plenty of other perfectly legitimate brands and services, including Dropbox, Sendgrid, Sharepoint, and OneDrive (to name but a few).
Indeed, just a few weeks ago we blogged about Canva, an online graphic design platform being used and abused in a very similar fashion. And Sendgrid, the popular email service provider used widely in Corporate America, recently reported that it had been battling a concerted credentials-stuffing attack that has compromised large numbers of accounts that have then been used to distribute large volumes of spam and phishing emails.
So, Slack is hardly alone in finding its service being misused by malicious actors. It has plenty of company these days, unfortunately.
So far we've seen relatively small numbers of malicious emails exploiting slack-files.com in phishing attacks. Moreover, these emails have been reported only in fits and starts since late June by customers using the Phish Alert Button (PAB), suggesting that the bad guys, at this stage, may still be experimenting with slack-files.com.
How It's Being Done
While Slack offers a variety of methods for uploading files to slack-files.com and sharing them publicly within Slack as well as externally, we're assuming that malicious actors are using a simple and obvious method for converting Slack into a malicious file repo.
In the method we suspect is being used, malicious actors would simply download Slack's client application, create their own private workspace, upload files within their instance of Slack, then create external links for those files that could then be re-used in phishing emails.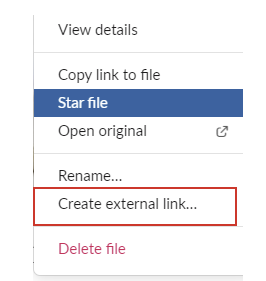
Although it's certainly possible that the bad guys are using compromised accounts of individual users within organizations already penetrated through phishing emails, we tend to doubt that compromised accounts lie behind what we're seeing for several reasons.
First, such accounts would have to be compromised in the first place, and these accounts could probably not be relied upon for extended periods of time. Second, any files uploaded with a compromised account would likely be visible to the user as well as the larger organization, raising the risk of discovery. Third, we expect that many if not most organizations (at least the ones that were minimally security conscious) would disable the option to create external links for files in order to prevent Slack from being abused to exfiltrate sensitive, proprietary data.
The method we've described above has the advantage of not being dependent on any other organization (beyond Slack itself). Moreover, it's not unknown for individuals not connected with businesses and organizations to download and use Slack to connect to public Slack channels or even create their own private workspaces. The method we suspect is being exploited would simply be a logical extension of the way Slack is already being used by countless individuals.
To be clear, we cannot verify that the method described above is in fact what lies behind the low volume of phishing emails exploiting slack-files.com reported to us by customers. It has enough advantages, though, to suggest that it may very well be how the bad guys are doing it.
Conclusion
You could be forgiven if your response to this was to shrug. But of course slack-files.com is being abused like this. If nothing else, that's an indication of the current state of phishing. It can seem an inevitable and almost unstoppable feature of everyday digital communication and life on the internet.
It does illustrate -- yet again -- just how determined and relentless malicious actors have become in sniffing out new means and methods for attacking the weakest link in your organization's security posture: its users.
Would your users even blink if they saw a file in a phishing email being offered up by a domain like slack-files.com? How many of them would even bother to check the link? By turns, how many would just blindly click and end up being led by the nose into a potentially devastating credentials phish?
If you're not quite sure (and if that uncertainty leaves you with a sinking feeling of dread in the pit of your stomach), then now is the time to step your users through New-school Security Awareness Training and begin testing them regularly with high-quality simulated phishing so that you find out just how bad your security problem is with the end users in your organizations and start to do something about it.
Cancel
 Here's how it works:
Here's how it works:
