.jpg?width=369&name=iStock-173890633%20(3).jpg) Security researchers uncover a marketing campaign that takes a page from the cybercriminal phishing handbook to “trick” pensioners to have an introductory call with their fund expert.
Security researchers uncover a marketing campaign that takes a page from the cybercriminal phishing handbook to “trick” pensioners to have an introductory call with their fund expert.
You would think that an established business would send out solicitation emails using their own business name, domain, etc. and be up front about who they are. Whether the recipient has done business with the sender or not, etc.
In this interesting use case of phishing tactics, PERA LLC, based in Nevada right off the bat takes on a familiar acronym. If your retirement is being managed by one of the various Public Employees Retirement Association companies, and even feels like an brand impersonation attack on the long-standing pension fund company, Colorado PERA.
Targeting the employees of U.S. municipalities, PERA LLC impersonated the municipality itself (e.g., placing the municipality name in the email subject), making the opportunity to speak with someone about their retirement feel like it’s company-sanctioned:
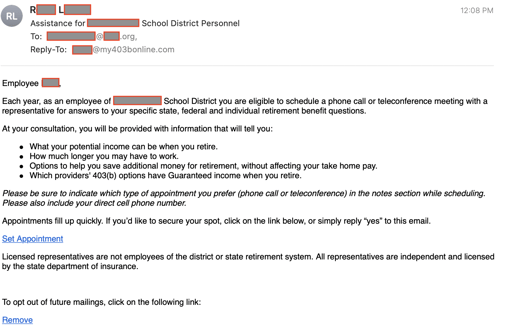
Source: PERA LLC
PERA LLC also used over 20 different PERA-related domain names to obfuscate who was really sending the email.
We’ve all seen items in the U.S. Mail attempting to appear “official” to obtain your business. But this is the first time I’ve heard about a company doing this using not just one, but many phishing tactics.
And while the end result here isn’t an infected environment or data being stolen, it’s important to teach users via Security Awareness Training on how to sport suspicious emails (even like this one) and realize they’re not legitimate.
 Here's how it works:
Here's how it works:




