 A new social engineering scam demonstrates how cybercriminals are both evolving their tactics while still using tried and true methods that just work to attain their goals.
A new social engineering scam demonstrates how cybercriminals are both evolving their tactics while still using tried and true methods that just work to attain their goals.
I’ve covered scams impersonating Office 365 I don’t know how many times. But it’s not very often you hear about a scam that uses LinkedIn as both its distribution medium and its’ credential target.
Last month, victim LinkedIn users received a message from one of their connections (which proved to have been compromised) that contained a link to a third-party website containing a “LinkedInSecureMessage” (which there is no such thing).
Victims are taken to a page displaying the following very official-looking page:

After pressing the “view document” button, they are presented with again, an equally convincing page.
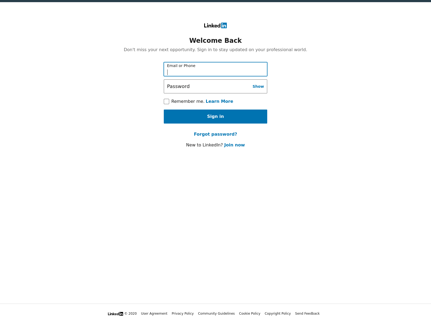
The scam here is to steal LinkedIn credentials, likely to be sold to another cybercriminal used to perpetuate additional scams. In this case, LinkedIn is merely the avenue of opportunity for the bad guy; it can just as easily be any other SaaS offering in the cloud.
Users need to stay vigilant with every cloud-based application they use; cybercriminals are always looking for the next site they can make use of to infiltrate to make a buck. Teaching users through Security Awareness Training will help to maintain that needed vigilance and lower the chance of users falling for even some of the best impersonation attacks around.
 Here's how it works:
Here's how it works:




