 Phil Goldstein at FedTech magazine had some concerning news.
Phil Goldstein at FedTech magazine had some concerning news.
"A top federal counterintelligence official says agencies must do more to harden their cybersecurity defenses, even if that means sacrificing some mission capabilities.
Over the last eight or nine years, of all the successful data exfiltrations and breaches that have hit the federal government and private industry, about 90 percent of them were the result of spear-phishing campaigns that targeted unsuspecting employees.
That's according to William Evanina, director of the National Counterintelligence and Security Center within the Office of the Director of National Intelligence.
"Until we clean that up, our adversaries need not get sophisticated with their intrusion apparatus," Evanina said during a keynote address on March 8 at a MeriTalk-hosted event, "Cyber Convergence: Security, the Cloud and Your Data."
"As American citizens, we have an unbelievable inability not to click on a link," he said, joking that any company that can absolutely prevent users from clicking on authorized links or opening unauthorized attachments would make a fortune.
On that front, agencies need to make progress. A Department of Homeland Security spokesperson told CyberScoop this week that more than two-thirds of agencies have adopted DMARC, which stands for Domain-based Message Authentication, Reporting and Conformance.
DHS mandated that, by Jan. 15, all agencies adopt some form of the protocol to prevent email spoofing, which can then be used in phishing campaigns to get users to click on links that will load malware. DMARC, DHS notes, gives agencies the "strongest protection against spoofed email, ensuring that unauthenticated messages are rejected at the mail server, even before delivery."
More broadly, Evanina argued, agencies and IT security leaders need to be willing to enhance cybersecurity protections at the expense of sacrificing some mission capabilities. Without that security, agencies will see their brands eroded, and with that, their value. IT leaders also need to develop crisis security plans and practice them regularly, he said.
Agencies Must Make Cybersecurity a Priority
Evanina said that his job, part of which involves providing counterintelligence outreach to government and private sector entities and issuing public warnings regarding intelligence threats to the U.S., involves "varying degrees of bad." However, he said, the government is doing an excellent job on the offensive front of counterintelligence activities.
Yet the threats the government faces are real and complex, Evanina said. "The threat we face now, today, is greater, more complicated, more sophisticated and more pervasive than ever before," he said.
The government's adversaries are "constantly learning from us and adjusting; they know our gaps and weaknesses," he said. The government always loves to defend against the last breach and not threats that will come in the future, Evanina said. "We rarely do predictive analysis of what the next breach is going to be."
Agencies now are being pushed to deliver flexible and fast services to users and citizens, Evanina said, with the mission delivered "at the click of a button," and security is often seen as an afterthought. The White House has pushed agencies to take a more risk-based approach to cybersecurity and protect high-value assets.
Evanina said the government must find a middle ground where the needs of end users are satisfied, but IT assets and data are secure.
"We have to be OK with sacrificing capability for security," Evanina said.
"We have no choice but to secure what we're doing, even if we have to sacrifice a little bit of mission," he continued, adding that IT leaders must do some "marketing" to convince employees that "it is going to be OK" if that happens. A security breach can fundamentally damage an agency's brand in the eyes of employees and citizens.
"It's all about [your agency's] brand," he said. "If you lose that, you lost everything." Read the rest of this article at FedTechMagazine: https://fedtechmagazine.com/article/2018/03/phishing-culprit-behind-vast-majority-data-exfiltration-intelligence-official-says

We've got something really cool for you: the new Phishing Security Test v3.0!
Sending simulated phishing emails is a fun and an effective cybersecurity best practice to patch your last line of defense… your users.
Find out the Phish-prone percentage™ of your organization with our free updated Phishing Security Test that now includes our New Industry Benchmarking. See where you stack up! Industry Benchmarking enables you to compare your organization’s Phish-prone percentage with others in your industry.
Find out how you are doing compared to your peers and see the difference 12 months can make after using the integrated KnowBe4 Simulated Phishing and Security Awareness Training platform!
With Our Updated Phishing Security Test: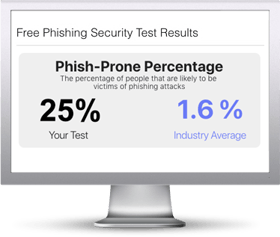
- You can customize the phishing test based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Start phishing your users now. Fill out the form, and get started immediately. There is no cost.





