By Eric Howes, KnowBe4 Principal Lab Researcher.
Phishing attacks have long been associated with malicious emails that spoof well-known institutions in order to trick users into coughing up credentials to banks accounts, email accounts, or accounts for major online services. Phishes that exploit the good name of trusted brands familiar to users have also been known to deliver ransomware, backdoors, and other malicious software designed to compromise the companies and organizations those users work for.
Spoofing well known institutions and brand names is old hat, though, and users have become increasingly wary of emails claiming to hail from familiar companies and organizations. In response, the bad guys have been refining their use of social engineering, the key to any successful phishing campaign.
Making the Extraordinary Seem Everyday
Over the past two years malicious actors have increasingly resorted to simpler, less flashy social engineering schemes designed not to raise eyebrows to but to capitalize on users' ingrained habit to click through attachments or links that give every appearance of being just more of the same dreary, business-related email content that fills their inboxes on a daily basis.
Thus, most of the major email-driven ransomware campaigns that we've seen over the past 6-9 months have been landing in users' inboxes under the pretense of dealing with invoices, P.O.s, IT-related messaging, and other ordinary business documents and topics, some of them very industry-specific. The social engineering hooks in such phishes are noteworthy only for just how unspectacular they initially appear. A few recent examples:
- Attached is the initial CD for my client (based on preliminary fees that you sent over). Can you please advise on revised/added fees (tax prorations, HOA dues, etc)?
- You are going to be billed USD 3,881.74 on your Mastercard balance soon. Take a look at the attachment for information.
- Your car loan is approved.
- Charge attached.
- Your order was completed in accordance with the agreement. Please see attached detailed estimates for each agreement article.
- We need your signature on this before we can settle.
- Please find attached the fully executed contract.
- Our HR Department told us they haven't received the receipt you'd promised to send them. Fines may apply from the third party. We are sending you the details in the attachment.
Such social engineering hooks are intended to provoke unthinking, habitual clicks from users inured to the avalanche of email that hits their inboxes day in and day out. Most are short -- some less than five words -- just like the majority of legitimate daily business email communication.
But even these cleverly designed phishes share a common problem: they are cold contacts, forcing users to refocus their attention on a new problem, a process that could raise their levels of awareness and alert them to something amiss. And, indeed, phishing emails are all by their very nature cold contacts.
But what if the bad guys could create the illusion of an on-going email discussion thread among office colleagues -- the kind of cozy, familiar situation in which few users would ever expect to be phished? In fact, that's just what we saw this week.
Starting from the Middle of Things
Over the past two days a number of our customers have reported receiving large numbers of a rather interesting phishing email.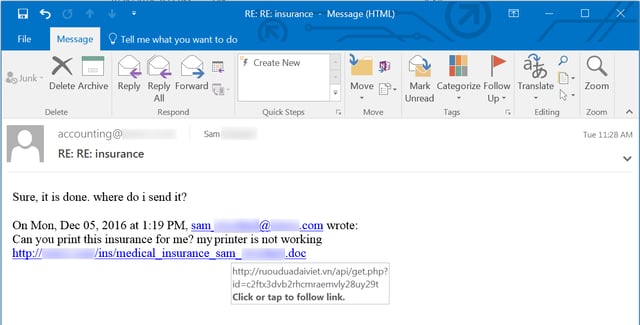
There are a couple of things to note about this email.
First, the email appears to be a conversation between two different employees -- one using a generic accounting email address within the company (whose name we've redacted) and a second being an individual employee named Sam. In fact, this entire email originated from outside the company being targeted. It is, in reality, a spoofed email thread.
Second, this is a targeted attack. The one named employee is real and the email address contained in the hyperlinked version of his name (only partially visible in the screenshot above) is that employee's actual email. Moreover, the visible link points to the company's own domain (while the actual underlying link, revealed by hovering the mouse, points to a Vietnamese domain). The bad guys obviously researched their targets before phishing them in order to create a credible, spoofed email thread purportedly involving real employees likely familiar to other users within the company.
Third, the social engineering hook involves an apparently innocuous request from a fellow employee. Who in a modern office environment hasn't encountered printer problems? Moreover, the link being dangled in front of users appears to offer access to personally sensitive information -- something that could prove irresistible to some people.
In short, this phish is a cleverly manufactured ruse designed to give users the impression that they have been mysteriously dropped into the middle of an ongoing discussion involving a document with personally sensitive information about another colleague working in the same office.
Just like any other phish, it's a cold contact. But it doesn't feel like one.
Things Get Real
Employees who click the link will find themselves downloading a malicious Word document that opens to a slickly designed macro warning screen offering the kind of "helpful" instructions that are now a staple among phishing campaigns pushing malicious Office macros: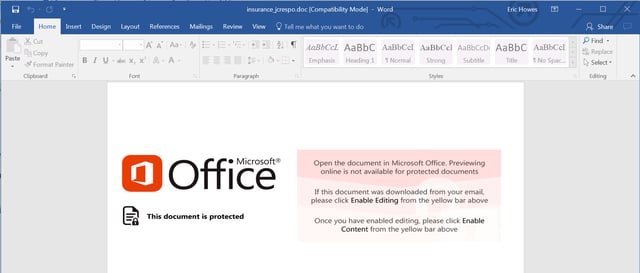
Users curious enough to follow the directions in that initial screen and enable macros will be kicking off a trojan downloader that pulls down a malicious .EXE from a domain registered just three days ago. That .EXE is then dropped in two locations: the \ProgramData and \Users\All Users folders.
After a reboot seven more files (all without file extensions) are added to those locations and a dodgy .DLL (probably extracted from one of those extension-less files) is automatically loaded by an instance of rundll32.exe.
The .DLL in question is, reportedly, a variant of Fareit -- a sophisticated password-stealing tool that scours compromised PCs for all manner of exploitable data and exfiltrates that data to malicious actors. On our test PC Sysinternals' TCPView revealed that the .DLL in question had established a connection with a site in Russia -- almost never a good sign -- on a port often left wide-open in corporate firewalls: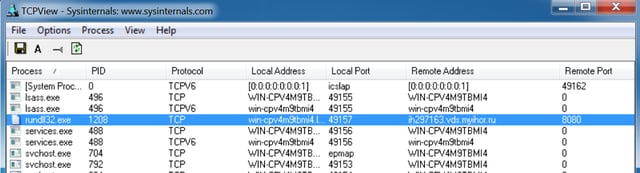
This phishing attack was undoubtedly the initial phase of a more extensive campaign to compromise the networks of targeted companies and exploit the resulting holes for monetary gain.
Helping Users Get Real
As noted earlier, we saw a large number of these malicious emails get reported to us by the employees of customers who have the Phish Alert Button (PAB) installed. Even though this attack used a rather unique social engineering hook, users who had been through KnowBe4's new school security awareness training nonetheless smelled a rat and clicked the appropriate button in Outlook, effectively notifying their own IT departments as well as KnowBe4.
This is exactly the kind of response you need from users when something as dangerous as Fareit sails right past all the rest of your security solutions and ends up lurking in your users' inboxes, tempting them to make one bad click and, in so doing, potentially bring the company down around their ears.
Too many users are taking the bait and clicking all the way through these ransomware traps. It's time to educate your users with new-school security awareness training and stop the madness.
Request a live, one-on-one demo today and see for yourself how easy this is.





