/Phishing-T.jpg?width=200&name=Phishing-T.jpg)
The beginning of 2019 has proven that data breaches in the health industry aren’t going anywhere. And from the intel on the breaches, phishing is playing a predominant role.
Patient Health Information (PHI) is very valuable – all kinds of information can be recorded: name, address, driver’s license, social security number, and insurance information. This data can serve as the basis for identity theft, insurance fraud, tax return fraud, and more. So, it’s no surprise that the health industry remains a target of cybercriminals.
Based on data from the U.S. Department of Health and Human Services, the top 5 Heath data breaches to date in 2019 total over 2 Million records:
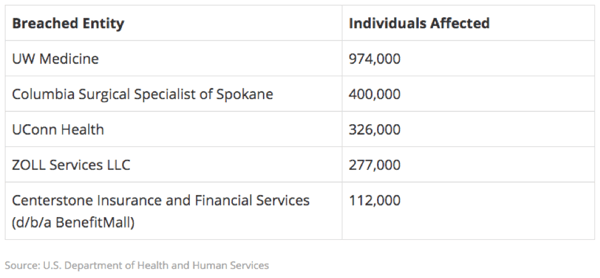
Of these 5 breaches, 3 of them (Columbia Surgical Specialists, UConn Health, and Cornerstone Insurance) stem from phishing attacks that directly resulted in either an exfiltration of data or a ransomware attack. While health-related organizations continue to attempt to prepare themselves for what looks to be a busy year of cyberattacks, those utilizing frequent phishing testing are seeing massive reductions in risk and malware infection.
The use of phishing testing, along with Security Awareness Training, help to raise the employee’s mindfulness around the use of good security practices as part of their daily job. Phishing testing provide the organization with a feedback look, helping them understand which employees are the least security-conscious and, therefore, present the greatest risk to the organization.
From the data above, it looks like the health industry should expect phishing attacks to continue. Putting security measures in place that specifically – and effectively – address phishing is imperative to keep data from being breached.






