 Fresh data on data breach costs from IBM show phishing, business email compromise, and stolen credentials take the longest to identify and contain.
Fresh data on data breach costs from IBM show phishing, business email compromise, and stolen credentials take the longest to identify and contain.
There are tangible repercussions of allowing your organization to succumb to a data breach that starts with phishing, social engineering, business email compromise, or stolen credentials – according to IBM’s just-released 2022 Cost of a Data Breach report.
Phishing and social engineering go hand-in-hand, with business email compromise and stolen credentials being outcomes of attacks, used as launch points for further malicious actions.
According to the IBM report, the average cost of a data breach in 2022 is $4.35 million, with an average of 277 days to identify the breach and contain it. That’s actually the good news. Why you ask? Because when you factor in the initial attack vector, it gets worse.
According to IBM, the following are the average data breach costs based on the initial attack vector:
- Phishing - $4.91 million
- Business Email Compromise - $4.89 million
- Stolen Credentials - $4.50 million
- Social Engineering - $4.10 million
Why so much? A lot of it has to do with how long threat actors act undetected as they move laterally within your environment, gain access to credentials and data, and exfiltrate your valuable data.
According to the report, the longest times revolve around attacks that involve your users:
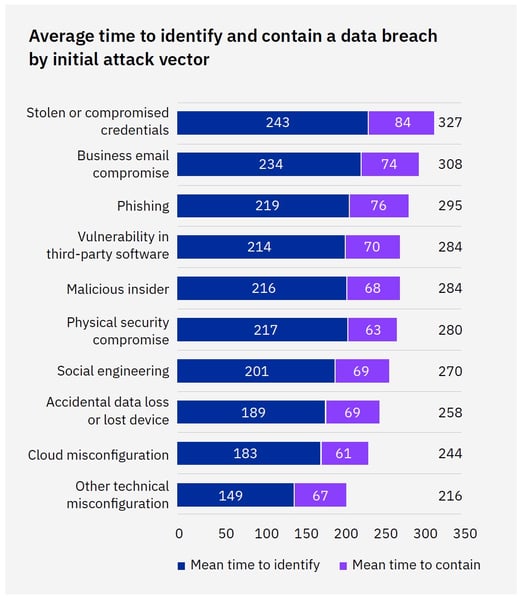
Source: IBM
With the average number of days to detection and containment being 277, it’s evident that stolen credentials, phishing, and business email compromise (the attack vectors your users play a role in!) push those “rookie numbers” up, giving attackers an additional 1-2 month’s time to continue their malicious activities.
Additional takeaways
- Employee security awareness training can cover 49% of the breach types
- Employee training saves USD $247K cost in terms of data breach impact cost (Page 20)
- Breaches in the public cloud were costliest for the organizations that don't invest in employee training and expect public cloud providers to take care of breaches.
We already know that phishing and BEC attacks focus on either stealing credentials or infecting endpoints, putting the user receiving the malicious email, phone call, text, etc. squarely in the middle of the discussion that results in these massive data breach costs.
Users need to play a role in your security strategy to help mitigate the risk of successful attacks through continual Security Awareness Training that teaches them how to identify suspicious content in email and on the web, helping to avoid any interaction that would result in a data breach.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




