Microsoft recently came across a threat that uses social engineering but delivers a different payload than the usual Office document with macros. Its primary purpose is to change a user’s browser Proxy Server setting which could result in the theft of authentication credentials or other sensitive information.
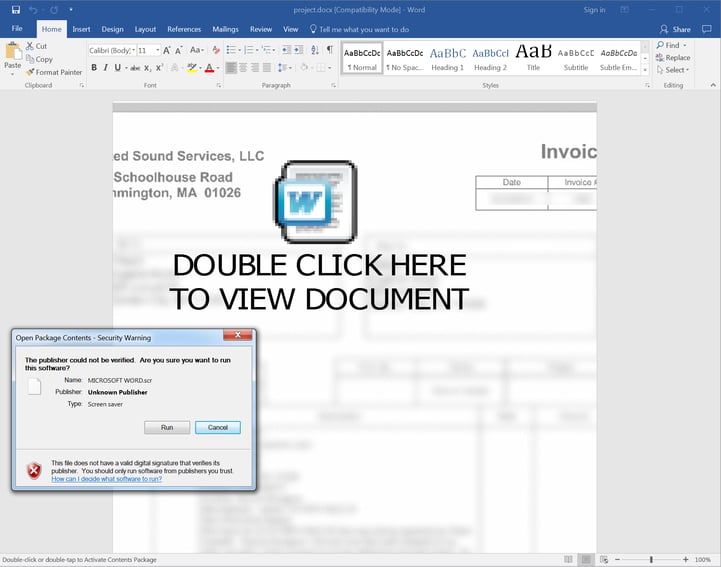
We've seen OLE embedded objects in malicious Word docs, but we haven't seen this particular new functionality from those objects (using an embedded script to maliciously configure proxy settings). All of the OLE embedded objects that we've encountered kick off scripts that pull down, then execute malicious files -- pretty much as documented in one of Microsoft's earlier blog posts.
Why Would They Do This?
At this point we are trying to figure out what would make the bad guy change proxy server settings, since the action required of the user to enable the malicious object is the same as that required to enable a more conventionally embedded macro, and the latter has proven a wildly successful ransomware infection vector for the bad guys.
It could be that OLE embedded objects are simply easier for standard AV engines to flag and block. Plus, a simple Registry setting will thwart the attack (see the last section in the blog post I linked to above).The Microsoft blog suggests two initial reasons: advertising (either to display ads on the victim's PC, much like adware does, or to perform click fraud); phishing (which doesn't make much sense -- why configure proxy settings to perform more phishing when you already had the opportunity to execute malicious code on the victim's PC?).
Changing Proxy Settings Is Much More Difficult To Detect
The only advantage we can see to the proxy settings approach is that it's a more passive approach (as opposed to running malicious code on the target PC) and much more difficult to detect than a malicious executable on disk or in memory.
One final thought: during the last two years we have been observing an increasing number of shady software companies operating out of Russia. They used the same tricks as more traditional adware companies (which are now largely located in and around Tel Aviv) to get their crapware on victims' PCs.
But the software they dropped was different than the crapware typically pushed by Israeli adware companies. Almost every single one of the Russian companies was dropping proxy programs of some sort on the victims' PC. And they were using those proxies to inject ads into users' browsers or to perform click fraud. Lots and lots of click fraud.
Free Phish Alert Button
Do your users know what to do when they receive a suspicious email?
Should they call the help desk, or forward it? Should they forward to IT including all headers? Delete and not report it, forfeiting a possible early warning? KnowBe4’s Phish Alert button gives your users a safe way to forward email threats to the security team for analysis and deletes the email from the user's inbox to prevent future exposure. KnowBe4's free Phish Alert for Outlook is an add-in you can download and deploy at no cost.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





