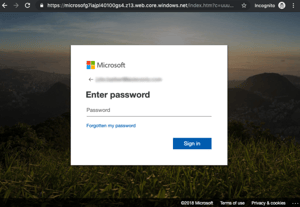
 Ray Shultz at MediaPost's EmailINSIDER wrote about a nasty new way that the bad guys are trying to establish trust: spoofing the return path and received email headers of Barracuda in an attempt to steal O365 credentials. Email security firm GreatHorn had the scoop on this attack.
Ray Shultz at MediaPost's EmailINSIDER wrote about a nasty new way that the bad guys are trying to establish trust: spoofing the return path and received email headers of Barracuda in an attempt to steal O365 credentials. Email security firm GreatHorn had the scoop on this attack.
So how did it happen?
“The attackers crafted the received headers so that it appears to have gone through multiple 'Barracuda' steps, before sending the email via a server designed to look like a Barracuda server." Among the phishing emails sent in this case was one purportedly coming from “Email Quarantine.” It included the message-id: noreply.barracudanetworks.com
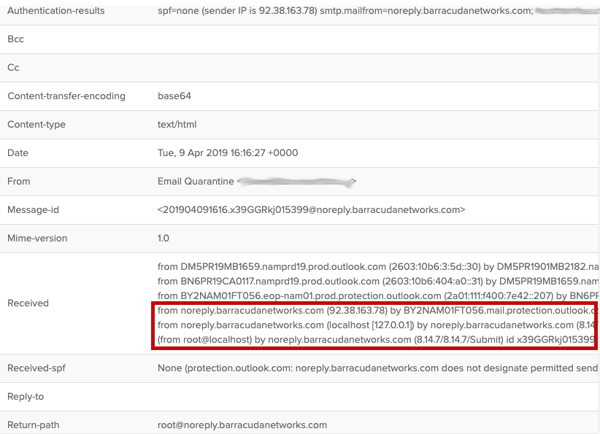
GreatHorn continued: "The attack “exploits a well-known security flaw in Google and Microsoft’s handling of authentication frameworks such as DMARC. While an organization can dictate how it wants DMARC failures and exceptions to be handled, Microsoft Office 365 typically ignores those directives and, at best, treats them as spam or junk instead of quarantining or rejecting them, making it more likely for the user to interact with such spoofs.”
You could easily see this replicated with another security company
GreatHorn says it discovered the attack last Thursday, then found a subset on Friday. The firm concludes: “While the spoofing victim in this case was Barracuda, you could easily see this strategy replicated using any other well-known security company to try and trick more savvy users.”
Yikes. Could be Symantec, McAfee, or KnowBe4. Keep your security awareness level set at HIGH!
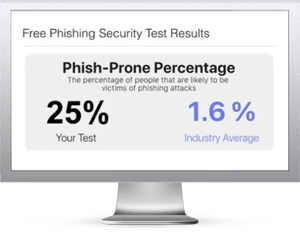
Free Phishing Security Test
Find out what percentage of your employees are Phish-prone™
Would your users fall for convincing phishing attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
 Here's how it works:
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organization compares to others in your industry
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





