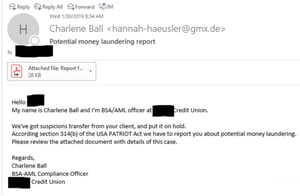
A spear-phishing campaign has been targeting Bank Secrecy Act (BSA) officers at a number of credit unions, according to Brian Krebs. The emails purport to come from other BSA officers, and contain PDFs that link to a malware-laden website. Each email has addressed its recipient by name, and said that the sender had identified a suspicious transaction, with details provided in the attached PDF.
The fact that the emails were only sent to BSA officers is noteworthy, since the identities of these officers aren’t supposed to be publicly known. Krebs says that many credit union sources suspect the data may have been obtained from the National Credit Union Administration (NCUA), which keeps a registry of credit union BSA officers. The NCUA released a statement saying that it had conducted a security review and didn’t find any evidence of a data breach.
Additionally, after Krebs’ original article was published, multiple sources confirmed that the emails were also “sent to BSA contacts at financial institutions other than credit unions, suggesting perhaps another, more inclusive, entity that deals with financial institutions may have leaked the BSA contact data.” It’s still not clear how the attackers got their hands on the information.
The US Secret Service in January sent an alert to financial institutions warning of a spike in successful, large-scale phishing campaigns. These campaigns are expected to increase as the US tax season approaches.
Employees need to know that attackers often use information from undiscovered data breaches to trick their victims. New-school security awareness training can teach your employees to be on the lookout for spear-phishing tactics. Full story at Krebs:




