Security researchers at Trend Micro have found a new type of ransomware that doesn’t encrypt specific files but makes the entire hard drive inaccessible. The malware has been named Petya and targets mainly companies.
As if encrypting files and holding them hostage is not enough, cybercriminals who create and spread ransomware are now resorting to causing blue screen of death (BSoD) and putting their ransom notes at system startup—as in, even before the operating system loads. Imagine turning on your computer and instead of the usual Windows icon loading, you get a flashing red and white screen with a skull-and-crossbones instead. Here is how it looks:
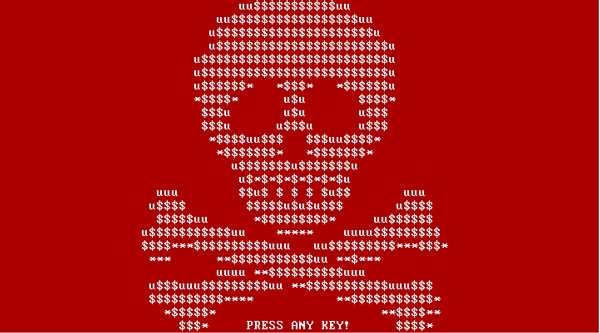
Here is a short Youtube video that shows it live.
Petya is distributed by sending spear phishing emails to Human Resources (HR) departments of companies with a link to Dropbox. The email states that the link is a resume (CV) but it’s actually an executable file. As soon as the file is opened the computer crashes and reboots. After the reboot, the user receives a message stating the computer is performing a disk analysis. In reality this is when the ransomware performs its job on the HDD.
The ransomware doesn’t encrypt the HDD but overwrites the Master Boot Record (MBR). After the disk analysis, a skull is shown together with a message stating the disk is encrypted. Through a Tor website it’s possible to purchase a decryption key for 0.99 Bitcoin ($412.50) which doubles after a week.
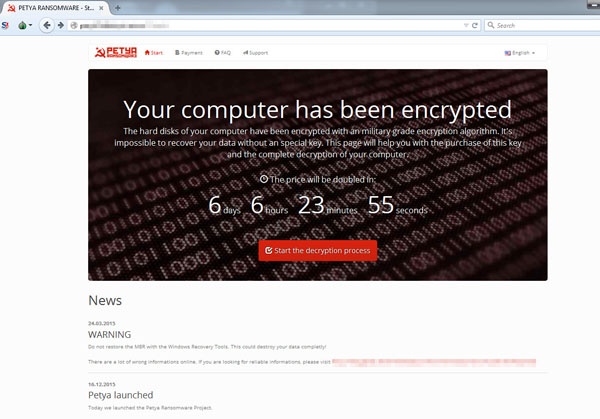
The overwritten MBR doesn’t allow starting the PC in safe mode and actual files don’t seem to be encrypted. It’s unclear whether it’s possible to restore the MBR to gain access to the HDD again.
F-secure looked deeper into Petya, to see what can be done to stop this threat, which is much faster than encrypting all the files, it simply encrypts the Master File Table, which means the operating system is not able to locate files. It installs itself to the disk’s master boot record (MBR) like a rootkit. But instead of staying covert, you get the red screen with instructions on how to get your files back. The infection vector is phishing emails sent to HR departments with a Dropbox link to "a resume".
Going after the MFT is a fast attack that takes far less time than encrypting data files, but the overall effect is the same – the data becomes inaccessible. F-Secure reported that Petya executes in two stages. The first stage is the main dropper, which:
- Infects the MBR.
- Generates a set of crypto keys, At this point also the special “decryption code” is prepared.
- Saves the disk crypto key and encryption code to disk for later use in the MBR infection code.
- Shuts down the machine without any warning to boot to MBR code.
During the second stage, the machine boots to MBR code, which:
- First checks to see if the disk is infected.
- If not, it will present a fake CHKDSK screen and will encrypt the MFT.
- Uses salsa20 for the encryption, and destroys the key after encryption.
- Presents the red “skull screen” and then the screen with Tor hidden service URLs, and the “decryption code”, which is an encrypted message only the server can open.
This is a whole new level (down) in encryption, and since the machine is rendered useless it is harder to pay the ransom. It remains to be seen if this criminal business model is going to be successful. It's pretty scary though, because the only way to get back the disk is to catch the salsa20 key inline of the infection process, using debuggers. Hardly possible for even experienced IT pros.
Hat Tip to Myce.
Get Your Ransomware Hostage Rescue Manual
 This 20-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
This 20-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
- What is Ransomware?
- Am I Infected?
- I’m Infected, Now What?
- Protecting Yourself in the Future
- Resources
Don’t be taken hostage by ransomware. Download your rescue manual now!
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/ransomware-hostage-rescue-manual-0

