 Researchers at ESET have come across phishing sites that try to steal PayPal logins along with a wide range of personal and financial information. The scam begins with phishing emails purporting to come from PayPal which inform recipients that an unknown device has accessed their account. The emails appear legitimate and convey a professional sense of urgency. The user is asked to click on a link in the email to verify their identity.
Researchers at ESET have come across phishing sites that try to steal PayPal logins along with a wide range of personal and financial information. The scam begins with phishing emails purporting to come from PayPal which inform recipients that an unknown device has accessed their account. The emails appear legitimate and convey a professional sense of urgency. The user is asked to click on a link in the email to verify their identity.
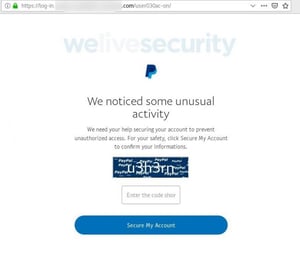
If a user clicks the link, they’ll be taken to a spoofed PayPal site that asks them to enter a CAPTCHA. The site uses HTTPS but has a suspicious-looking URL, which could tip off observant users. The CAPTCHA page also contains some oddly phrased English, asking users to “confirm their informations.” After entering the CAPTCHA, users will be asked to enter their PayPal credentials.
At this point, the attackers can already steal a victim’s money if their account doesn’t have multi-factor authentication enabled. However, the attackers in this case assume that if the victim has come this far, it’s worth trying to squeeze more information out of them. The next several pages ask the victim to update their billing address by entering their credit/debit card details along with their name, full address, phone number, date of birth, and mother’s maiden name. Finally, the victim will be asked to enter their email password in order to link their email account to their PayPal.
ESET notes that this scam relies solely on social engineering, so users can defend themselves if they know how to recognize suspicious emails, links, and websites.
“Much like other threats in cyberspace, phishing attacks come in various shapes and sizes and continue to evolve,” the researchers write. “As the example shows, however, social engineering tactics remain at the heart of such scams. After all, by preying on human weaknesses, cybercriminals usually take the path of least resistance. For the victims, even a momentary lapse in judgment or a short moment of distraction can have far-reaching and deleterious consequences.”
New-school security awareness training can enable your employees to spot social engineering tactics with realistic examples of phishing attacks. ESET has the story:
https://www.welivesecurity.com/2019/12/20/scam-wants-more-than-paypal-logins/
 Here's how it works:
Here's how it works:




