Passwords serve as the foundation for most security today. But security vendor SpyCloud have recovered over 3.5 billion credentials, demonstrating just how insecure they really are.
We’d like to think that in this day and age, users are aware that they need to use secure passwords. Putting aside cyberattacks focused on tricking users into providing credentials, the passwords themselves should be complex enough that they’re not easy to break.
But, according to SpyCloud’s Annual Credential Exposure Report, released last month, passwords (and their encryption) are anything but secure.
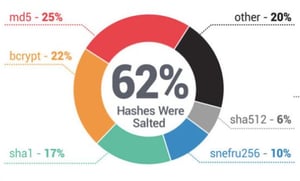
SpyCloud was able to recover over 3.5 billion credentials from over 2800 breached sources. They decrypted nearly 90% of all the passwords collected, yielding 2.3 billion plaintext passwords. According to the report, the cracking of the passwords was easy. The encryption methods used aren’t a challenge for the sophisticated software used by cybercriminals.
And to boot, the passwords themselves weren’t very secure – adding to the ease of decryption. Passwords like “12345”, “password”, “iloveyou”, and “qwerty” continue to top the list of the most commonly used.
So, what’s to blame when it comes to exposed credentials?
There are a few factors:
- Encryption – organizations hosting credentials for cloud-based applications need to be using the highest possible levels of encryption.
- Policy – organizations should require secure passwords with minimum length, complexity, and change frequency requirements.
- Awareness – users themselves aren’t the slightest bit concerned about the security of their passwords. Organizations should use Security Awareness Training to continually update users on security best practices, details on attack methods used, and how users can be vigilant at work and home to not become a victim.
Are your user’s passwords…P@ssw0rd?
Employees are the weakest link in network security, using weak passwords and falling for phishing and social engineering attacks. KnowBe4’s complimentary Weak Password Test (WPT) checks your Active Directory for several different types of weak password related threats. Here's how it works: 
- Reports on the accounts that are affected
- Tests against 10 types of weak password related threats
- Does not show/report on the actual passwords of accounts
- Just download the install and run it
- Results in a few minutes!
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





